人懒,懒得重新写writeup,写了一些觉得蛮不错的点,其中几题借鉴了下大佬的。
Hackon18
Junior/Facche
Junior/Facche_Salad Upgrades
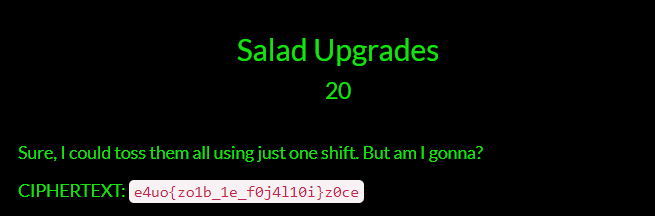
给出字符串 e4uo{zo1b_1e_f0j4l10i}z0ce
这个还是稍微有点特殊,每个字母的偏移量是在这个字符串的第几位,脚本解一下:
1 | #-*-coding:utf-8 |
得到答案d4rk{th1s_1s_r0t4t10n}c0de
Misc
Misc_EtherHide
打开MyStorage.sol有以下代码
1 | pragma solidity ^0.4.24; |
看不懂没关系,题目给了
- Network :
Ropsten Test Network - Contract Address :
0x94f23F189583e828E73573905A19d93E21D0E957
根据第一个提示,谷歌一波发现网址:https://ropsten.etherscan.io/,这是个此题以太坊的工作站点
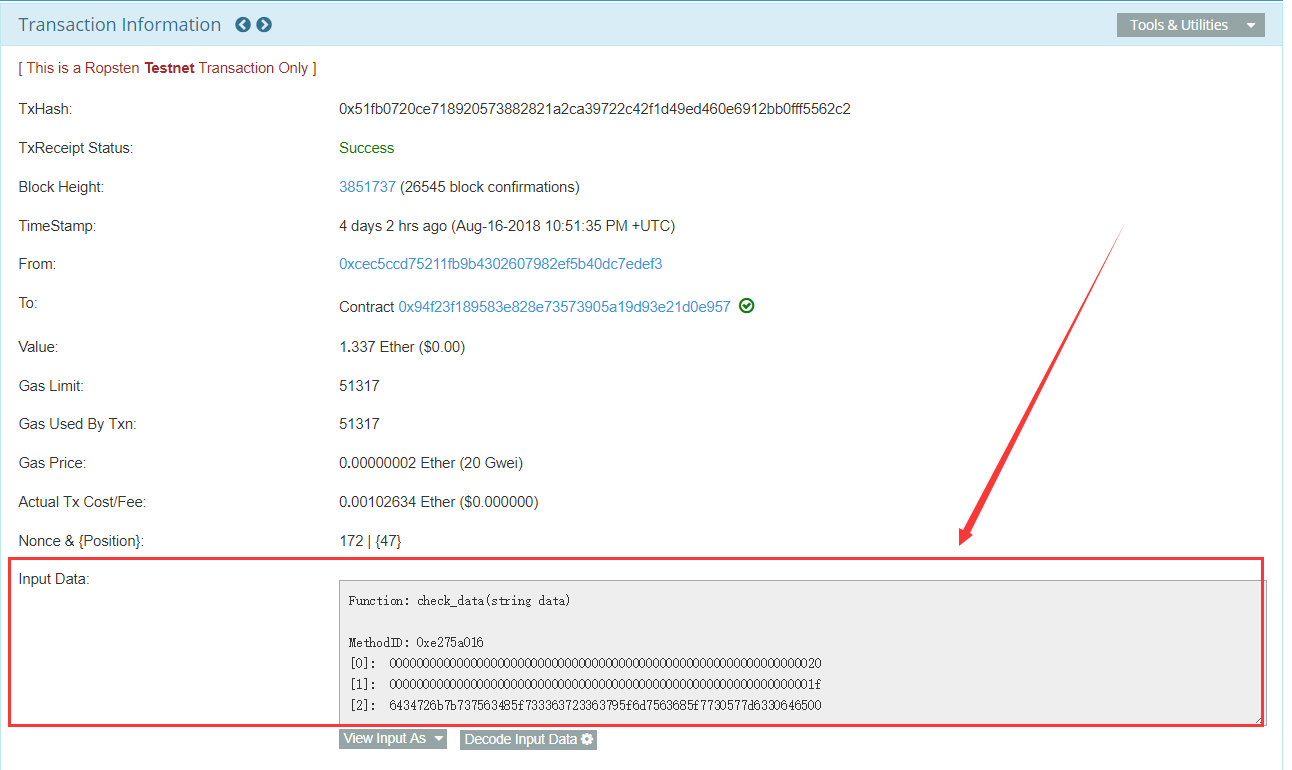
第二个提示告诉合同地址,于是打开网页https://ropsten.etherscan.io/address/0x94f23F189583e828E73573905A19d93E21D0E957
其中翻阅下,会找到一个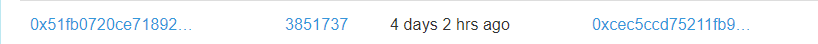
打开,Input Data中的数据,winhex打开,16进制转ASCII,得到答案

Misc_CryptoRevSalad
这题做的有点难受,给了个数据包,三板斧分析,简单分析了下
tcp流3是明文字符,给了以下信息
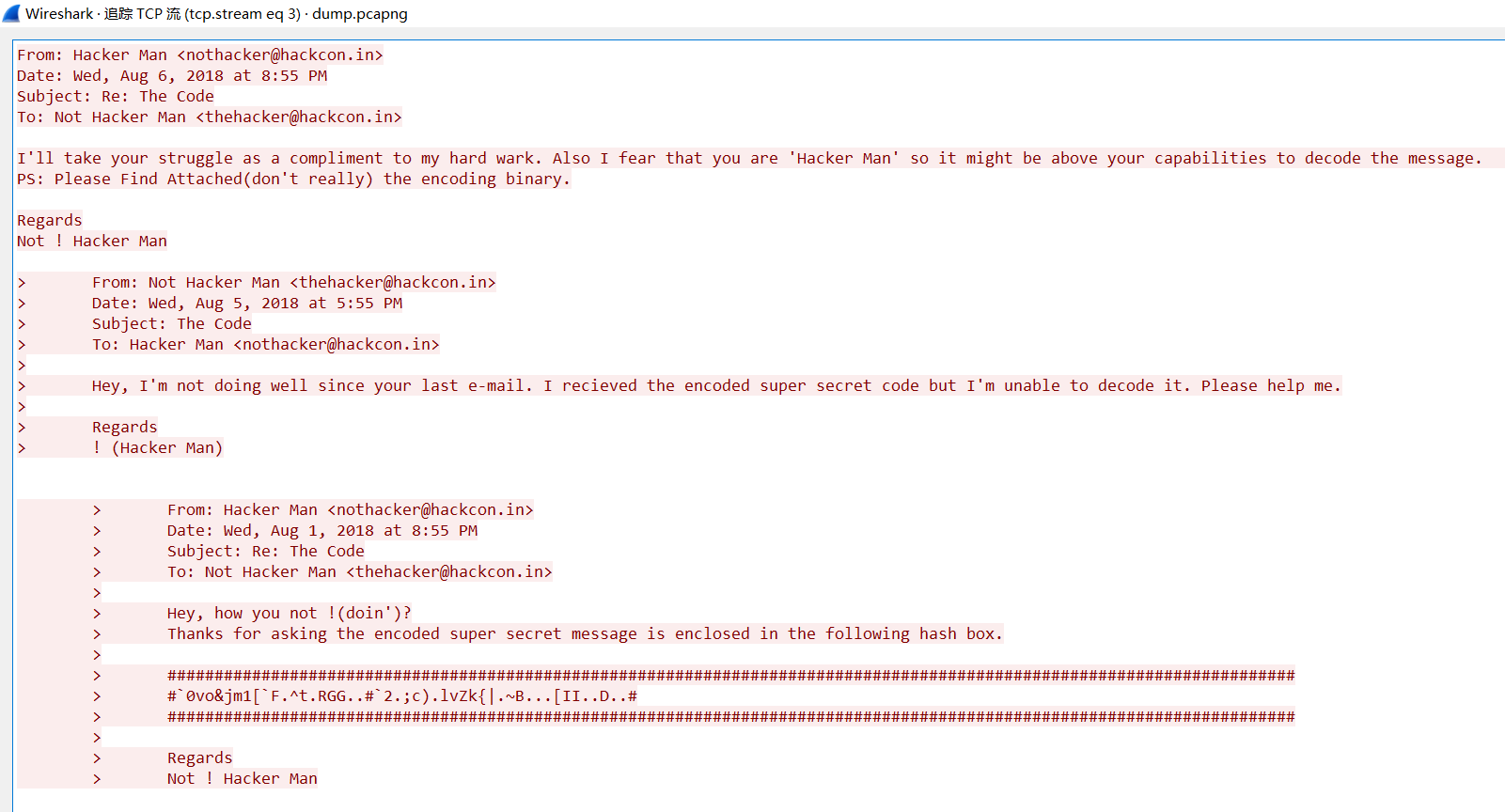
再看看tcp流5
看到有种熟悉的感觉,实际上就是个zip的16进制,不过是每个字节颠倒的,把这个保存为zip.txt,代码操作一番
1 | #-*—coding:utf-8 |
得到结果,复制到winhex里,保存zip.zip文件,打开,发现个ELF文件,有的玩
此题有待研究,期待待续咯!!!
补:发现此题writeup,后面完善
Crypto
Crypto_Diversity
复制下
b1001000 x69 d33 d32 o127 b1100101 o154 o143 b1101111 o155 o145 d32 o164 d111 d32 x48 b1100001 x63 o153 b1000011 o157 x6e d39 o61 b111000 x2c d32 d111 b1110010 d103 d97 x6e o151 x73 d101 d100 o40 d97 b1110011 b100000 x70 o141 o162 x74 d32 x6f x66 b100000 o105 b1110011 x79 b1100001 d39 d49 b111000 x20 b1100010 d121 b100000 x49 o111 b1001001 x54 b100000 b1000100 x65 x6c o150 x69 b101110 x20 o111 d110 b100000 o143 d97 d115 o145 o40 b1111001 b1101111 x75 b100111 x72 x65 x20 x73 x65 b1100101 b1101011 x69 o156 x67 d32 b1100001 o40 o162 x65 o167 b1100001 o162 o144 d32 x66 d111 x72 b100000 o171 x6f d117 b1110010 o40 d101 x66 x66 x6f x72 d116 o163 x2c b100000 d104 b1100101 d114 o145 x27 d115 x20 b1100001 d32 d102 d108 b1100001 x67 x20 x3a b100000 o144 x34 o162 x6b x7b o151 d95 d87 o151 x73 b100011 d95 x41 o61 x6c d95 b1110100 d52 d115 b1101011 d53 o137 o167 x33 d114 o63 o137 d116 b1101000 o151 o65 x5f x33 d52 o65 o171 o137 x58 b1000100 b1000100 b1111101 x63 d48 d100 d101 d46 b100000 o101 x6e b1111001 d119 b1100001 b1111001 x73 b101100 x20 o150 d111 b1110000 b1100101 o40 x79 o157 d117 b100000 b1101000 o141 x76 x65 b100000 d97 x20 o147 d111 b1101111 d100 b100000 b1110100 b1101001 d109 b1100101 d32 x3b x29
观察到x、b、d、o字样,估计就是进制之间的转化,然后转成ASCII码对应的字符。写个脚本
1 | #-*-coding:utf-8 |
输出结果
Hi! Welcome to HackCon'18, organised as part of Esya'18 by IIIT Delhi. In case you're seeking a reward for your efforts, here's a flag : d4rk{i_Wis#_A1l_t4sk5_w3r3_thi5_345y_XDD}c0de. Anyways, hope you have a good time ;)
Crypto_Light N’ Easy
题目内容:
01001110-00100000-00111010-00001100-11011110-00011110-00000000-01100000-00101010-01111010-00100000-11110110-00111010-00000000-11111110-00001100-00111000-11011110-00000000-10111100-00001010-11011110-11011110-00101010-00000000-01110110-11011110-00001100-00001100-00111010-01010110-00000000-11111100-00001010-11111010-00101010-11110110-11011110-00000000-11101110-11011110-01111011-00000000-10001110-00001100-11111010-11110110-00000000-00100000-10110110-00000000-00011101-10011111-01111011-10110111-11111110-00001010-00100000-00101010-11110111-01111000-00111010-01100111-10001100-00111011-10101010-11011110
hint.jpg
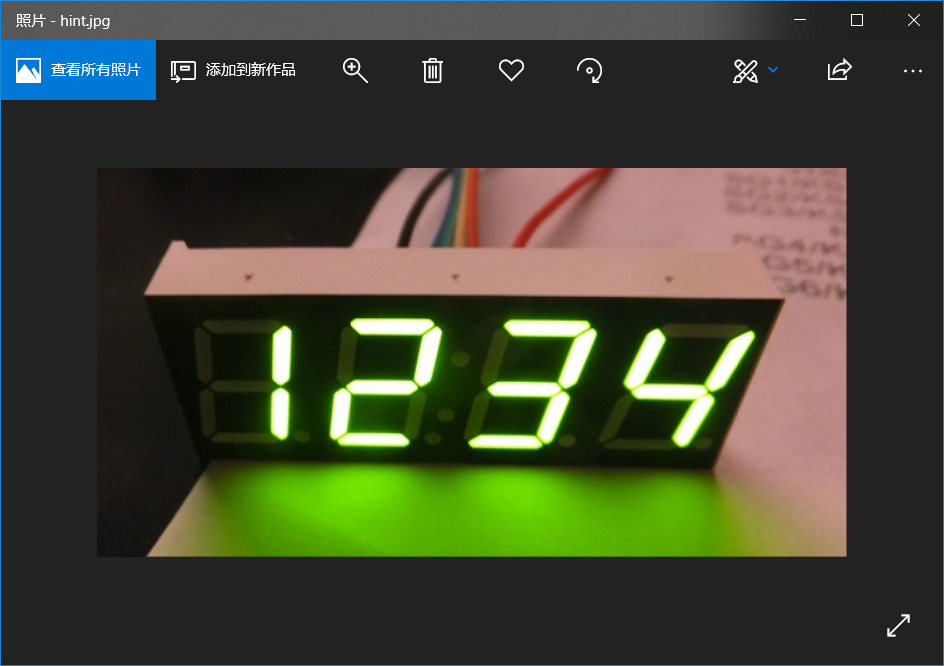
下意识二进制转化,然后发现错了,国外网站搜索一波
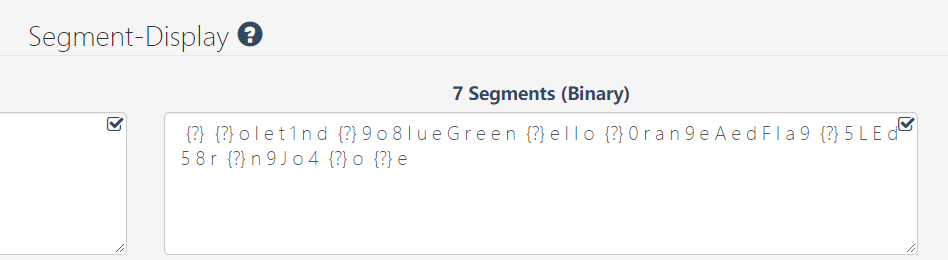
嗯,很像对吧,然后学习了下https://www.wikiwand.com/de/Segmentanzeige
其实每个8位的值都是按以下字母的顺序对应的
1 | b |
写个脚本
1 | enc = '01001110-00100000-00111010-00001100-11011110-00011110-00000000-01100000-00101010-01111010-00100000-11110110-00111010-00000000-11111110-00001100-00111000-11011110-00000000-10111100-00001010-11011110-11011110-00101010-00000000-01110110-11011110-00001100-00001100-00111010-01010110-00000000-11111100-00001010-11111010-00101010-11110110-11011110-00000000-11101110-11011110-01111011-00000000-10001110-00001100-11111010-11110110-00000000-00100000-10110110-00000000-00011101-10011111-01111011-10110111-11111110-00001010-00100000-00101010-11110111-01111000-00111010-01100111-10001100-00111011-10101010-11011110' |
运行得到结果
最后结果
1 | d4rk{L.E.d.s.Bring.Joy.To.me}c0de |
Crypto_Ron, Adi and Leonard

rsa.txt内容如下:
1 | n = 744818955050534464823866087257532356968231824820271085207879949998948199709147121321290553099733152323288251591199926821010868081248668951049658913424473469563234265317502534369961636698778949885321284313747952124526309774208636874553139856631170172521493735303157992414728027248540362231668996541750186125327789044965306612074232604373780686285181122911537441192943073310204209086616936360770367059427862743272542535703406418700365566693954029683680217414854103 |
会发现e贼大,好的Winner爆破
1 | import math |
运行脚本,得到答案d4rk{r3p34t3ed_RsA_1s_f0r_n00bs}c0de
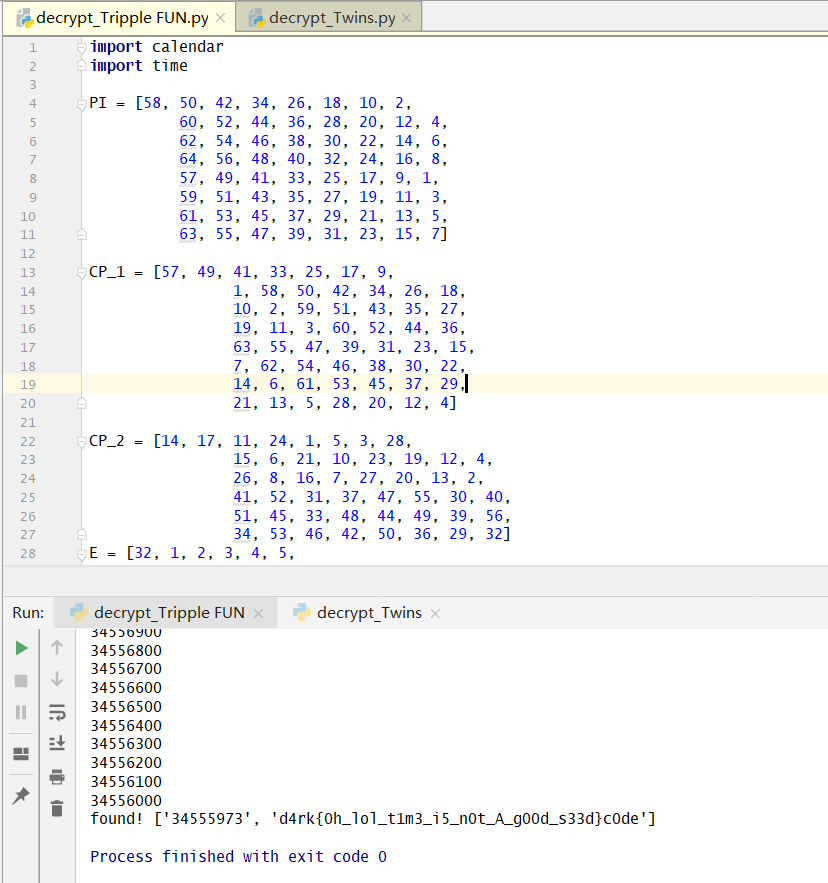
Crypto_Tripple FUN
题目文本内容
|\xb3Wm\x83\rE7h\xe3\xc0\xf1^Y\xf0\x8d\xa6I\x92\x9b\xa5\xbc\xdc\xca\x9d\xcd\xe9a0\xa3\x00\xf2\x13\x16]|\xae\xd8\x84\x88
这题嘛,有点意思,DES解密 ,解密代码会比较长
1 | import calendar |
脚本爆破半天,得到答案d4rk{0h_lol_t1m3_i5_n0t_A_g00d_s33d}c0de
Steg
Steg_Twins
经过比较,file1和file2两个文本文件的长度一样,再仔细观察,找出两个文本的相同的字符,拼接出来就是flag
1 | #coding:utf-8 |
运行得到结果
d4rk{lo0king_p4st_0ur_d1ff3renc3s}c0de
Steg_Steg It Up
打开下载的图片
神奇Stegsolve试水一波,发现一排的二维码
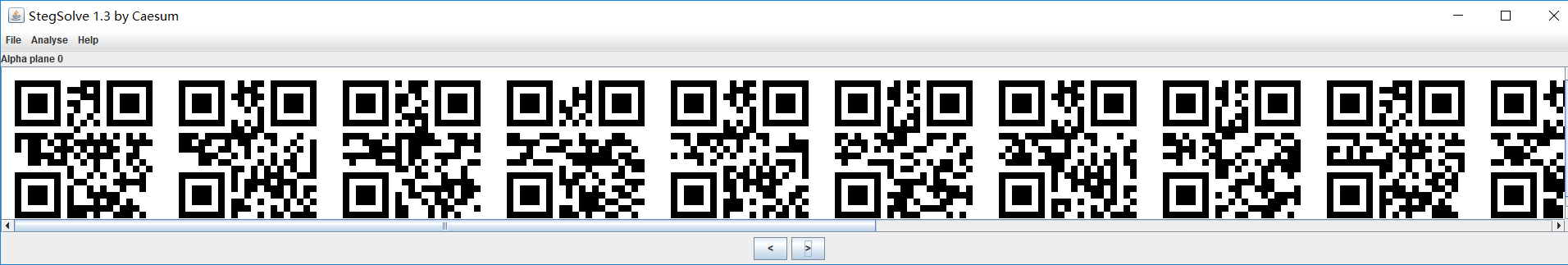
一个一个扫扫咯
得到答案d4rk{s000_m4ny_0f_7h3m_l0l_1_h4v33_t0_m4k333_th3_fl4g_l0ng_f0r_n0000_r3450n_1m40}c0de